With ransomware attacks steadily rising, merely following Industry best practices may not be the only solution to counter ransomware attacks, instead organizations must understand the modus operandi of such attacks, intent, and countermeasure to effectively dealing with ransomware attacks.
 Regardless of a business’s size or location, almost every industry is under malicious actors’ prying eyes. Anyone could encounter a situation where all their systems are locked up, with each screen displaying a ransom demand. With no way forward and the organization’s information infrastructure under hostage, its financial resources and reputation could be at stake when the entire organizational network is under a ransomware attack. There could be no alternative than to shell out the demanded ransom to get the systems unlocked. It’s time both SMEs (Small Medium Enterprises) and SMBs (Small and Mid-sized Businesses) became aware of the consequences of such ransomware attacks. It can help devise intelligent mechanisms to dodge the threat and safeguard the confidentiality, integrity, and availability of your organization’s information assets.
Regardless of a business’s size or location, almost every industry is under malicious actors’ prying eyes. Anyone could encounter a situation where all their systems are locked up, with each screen displaying a ransom demand. With no way forward and the organization’s information infrastructure under hostage, its financial resources and reputation could be at stake when the entire organizational network is under a ransomware attack. There could be no alternative than to shell out the demanded ransom to get the systems unlocked. It’s time both SMEs (Small Medium Enterprises) and SMBs (Small and Mid-sized Businesses) became aware of the consequences of such ransomware attacks. It can help devise intelligent mechanisms to dodge the threat and safeguard the confidentiality, integrity, and availability of your organization’s information assets.
Some Key Statistics On Ransomware Attacks
A business owner cannot merely shrug off such threats in the digital space. They have to be adequately aware of the matter and consider mitigation measures to stay clear of ransomware. The below graph shows a rise in the percentage of organizations that faced ransomware attacks during the 2017-2019 period.
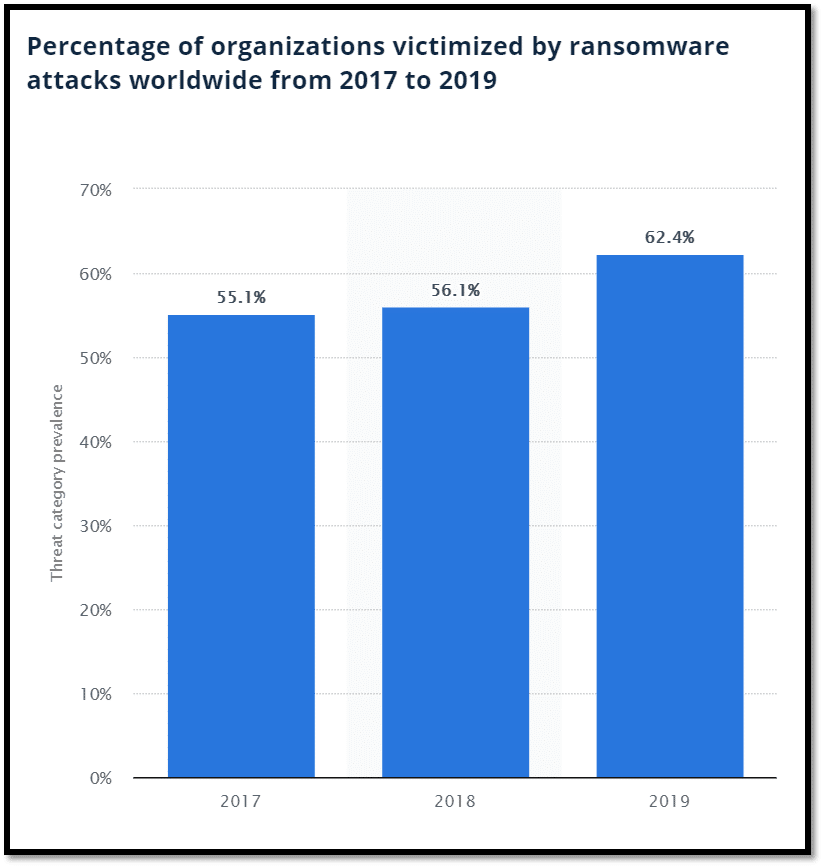
The facts and figures listed below help to get a broader idea about the looming vulnerabilities.
- Over the years, ransomware attacks have gained popularity among malicious actors, with a 350% increase in 2018 alone.
- In the last quarter of 2018, the Ryuk ransomware showed around 543% of increased detection.
- In 2019, new variants of ransomware grew by 46%.
- 68,000 new mobile ransomware Trojans were identified in 2019.
- As many as 205,000 businesses have lost their access to online resources and files in 2019.
- Presently, 65% of ransomware attacks take place through phishing.
- Estimates reveal that in 2021, a ransomware attack is likely to occur every 14 seconds.
- In 2019, the average cost of a ransomware attack was $133,000.
- In 2021, ransomware costs are likely to add up to around $20 billion.
- Around 50% of employees working with IT organizations believe that their organization is not yet ready to withstand a ransomware attack.
What Is A Ransomware Attack? How Does It Take Place?
Ransomware is among the most significant cybersecurity issues of the decade. It is among the most potential adversaries an organization is likely to encounter. Ransomware can be defined as malware or malicious software designed to encrypt documents and files of a business’s information network. Starting from a single information system, it can affect an entire network, including the servers. In a ransomware attack, the malicious actors often leave the victims with no other option than to pay ransom to unlock their data and online resources.
Once anyone becomes a victim of a ransomware attack, the malicious actors would display instructions to obtain the decryption key by making the payment. In most cases, enterprises need to shell out the amount in cryptocurrencies, such as Bitcoin, which enable the threat actors to remain anonymous. The ransom may range from a few hundred dollars to thousands of dollars, and in some cases, it has gone up to millions of dollars. Below is a list of the most common modes of ransomware attacks:
- Email Attachments
Emails are susceptible to ransomware attacks. Malicious actors might inject ransomware into a network through emails. These emails may come with a familiar subject line to disguise them as legitimate. The user unsuspectingly opens the emails, downloading the malicious files.
Most employees fail to differentiate between regular documents and ransomware. However, ransomware deploys file extensions like ‘.scr’ and ‘.exe.’ If an employee downloads these files or opens them, the malware would get installed in the system.
- Drive-By Downloads
These downloads that occur without the users’ permission or knowledge can also install ransomware into the information systems. The ransomware gets injected as soon as someone opens one of the malicious sites designed for the purpose. And business owners are often oblivious when the system is infected.
Currently, malicious actors have flooded cyberspace with such malicious websites that resemble traffic-generating popular portals. The user might make an error while entering the name of a popular site that opens the malicious portals. Eventually, the drive-by downloads capitalize on the network vulnerabilities and install the ransomware in the system.
- Botched URLs
This mode of ransomware attack also uses emails. In this case, the attackers lure employees into clicking on the URL sent through emails, which is camouflaged somehow. For instance, the employees may receive an email containing a link to check their tax filing status.
The fake URL would appear so realistic and close to the original one that it would be difficult for the employees to detect the fraud. A single click on such a URL can get the ransomware installed in the system.
- External Storage Devices
At times, ransomware infection may occur by sharing external devices like hard drives or USB flash drives. However, this type of attack can also be intentional, and plugging in the storage device results in ransomware installation. Once it gets installed, it would cripple the entire system. It is relatively common with startups these days.
What Are The Countermeasures To Take If A Ransomware Hits The Organization?
During the trying moments following an attack, the extent of damage would largely determine the course of action. Enterprises partnering with reputed professionals for a managed IT system can address the situation better since they will have a backup for the files. It is advisable not to pay any ransom to malicious actors, which is possible when there is an appropriate backup. Alternatively, there are specific strategies that can prove handy during a ransomware attack, as mentioned below.
- Never Pay Ransom
The first rule is to never pay the ransom. There is no guarantee that the malicious actors will not vanish with the amount, leaving the data still locked. Besides, despite spending the ransom, one can face yet another attack anytime.
The best way to manage ransomware attacks is not to entertain the attackers. Given that one is already aware of these vulnerabilities, the most logical approach to thwart ransomware attacks is to ignore their demands. When there is a backup in place and payment is refused, the attackers would have to look for an alternative target.
- Isolate The Affected Systems
In general, the attackers infect one system through malware, which eventually takes the entire information network down. If you are able to detect the vulnerability, you must immediately isolate the infected system from the network. It helps in keeping the other files shared through the network secure.
- Disable Maintenance Tasks
When there is a ransomware attack, make sure to disable the maintenance tasks that are automated. These include log rotation and removal of temporary files. The reason is that such changes may interfere with the files that the forensics team and investigators might find beneficial. The file logs may have certain clues about the origin of the infection. Besides, some unsophisticated ransomware variants leave temporary files that contain encryption keys.
- Secure The Backups
When there is no collaboration with IT professionals for managed systems and enterprises deal with storage tasks themselves, it is imperative to secure backups. During the redemption process, one would find these backups crucial. Currently, malicious actors are even designing ransomware that targets backups. During a ransomware attack, seek professional IT support to secure the backups or disconnect them from the network. It would be logical to lock down the access to these files until resolving the issue.
- Contact The Cyber Insurance Provider
In the wake of rising online threats, ambitious enterprises are ready to purchase cyber-insurance policies. In case you have already insured the systems against cyberattacks, you must reach out to the insurer immediately to assess the damage. Eventually, you can file a claim to recover the monetary losses.
However, one needs to contact the insurer before evaluating the damages. Most of these insurers are equipped with forensic analysis tools. They would help with answers to the prime questions regarding the cyberattack. Besides, if any of the clients sue the enterprise for data breach or violation of the regulations, these professionals can offer valuable advice.
How Can Businesses Safeguard Their Information Assets From A Potential Ransomware Attack?
Businesses must resort to all mitigation methods and safeguards possible to thwart ransomware attacks. Below given are a few of the best practices to secure the information system from the threat.
- Periodic Review Of IT Security
Arranging regular audits for the security of IT infrastructure is highly recommended. It would help detect possible loopholes in security and address grave issues. One might install anti-phishing software or antivirus to strengthen the security of the system. Consulting a professional managed IT services provider would also be a wise decision.
- Employees Training, Education, And Awareness
Amidst the digital threats, startups and established organizations need to train their employees on malware and ransomware attacks’ essential concepts. Educating staff with the best practices is a viable mechanism to avoid such attacks altogether. From time to time, arranging workshops or training sessions helps ensure that employees do not open suspicious emails, links, or documents in the workplace.
- Regular Data Backup And Testing
Malicious actors design ransomware to take online resources and data hostage. Under such threatening circumstances, no business owner can afford to compromise their data integrity. It would be advisable to maintain data backups. You might store the backups, preferably on servers at remote locations. It ensures that your organization can restore the data seamlessly following a ransomware attack and ensure business continuity. Presently, many organizations are using cloud storages to store their data securely. It is advisable to seek professional support for data backup if you are new to such technologies.
- Update & Upgrade The Information Systems
Ransomware can enter a system through various means by exploiting an outdated program’s vulnerabilities. Look out for possible updates in the workplace’s local information systems and update the anti-malware, anti-phishing tools, and antivirus to their latest versions. Ensure that the IT department installs the latest patches in the operating systems that carry a defense against various ransomware types.
- Deploy Advanced Tools
It is advisable to go beyond the local IT infrastructure to protect your organization’s valuable digital assets. Advanced AI-ML (Artificial Intelligence-Machine Learning) based systems can help organizations predict anomalies and secure an organization against ransomware attacks. Advanced cloud-based solutions also can help an organization replicate critical data in several locations to make disaster recovery amazingly easy, nullifying the impact of any possible ransomware attack.
- Effective Identity And Access Management
Enterprise leaders must incorporate strategic identity management and access control norms to secure their digital assets. Each employee working with the organization should be entrusted with well-defined permissions and roles. The employees must access data based on policies like ‘need to know basis’ and ‘segregation of duties.’ For example, an employee working in the marketing department should have no access to data in the financial files. With restricted access to information, the scope and impact of the cyberattack would also be lower.
- Securing Remote Access
One cannot rule out the possibility of remote access malware attacks. It is crucial to secure remote access to a system. Being the owner of a startup or established enterprise, one could disable remote access if one does not require the feature at the moment.
When there is a need to establish remote access, make sure to deploy secure VPN networks, enabled with Multi-factor authentication (MFA) to minimize the chances of unauthorized access to data. Besides, limit access to employees who need it for their assigned tasks. One might also go for network segregation to address security challenges.
Final Words
Any possible countermeasure to address threats like ransomware involves robust preparation to encounter such attacks. Maintaining a proactive approach would significantly slash down the risks of attacks. Even if the organization becomes a victim of a ransomware attack, proper data backups and preventive measures will nullify the loss. An enterprise might also consider seeking professional IT support to initiate the recovery process if there is an attack and must educate its employees adequately to thwart threats to the maximum.
BACK TO MAIN PAGE
