Those days are long gone when just having a strong password was sufficient for an organization’s or individual’s security needs. Today, malicious actors can crack a password in seconds using sophisticated algorithms. Dual authentication can ensure better security for your business by providing a second layer of defense.
 Ever since the advent of the internet, passwords have been the gateway to every system and account online. Passwords and PINs are ubiquitous and are used to securely access systems, email, social media accounts, and even door locks. However, these passwords alone aren’t the ideal security measure when a cyber attack is launched every fourteen seconds! It isn’t surprising to note that over 80% of all data breaches in 2019 resulted from password hacks. The answer to overcoming these vulnerabilities is dual authentication or two-factor authentication (2FA).
Ever since the advent of the internet, passwords have been the gateway to every system and account online. Passwords and PINs are ubiquitous and are used to securely access systems, email, social media accounts, and even door locks. However, these passwords alone aren’t the ideal security measure when a cyber attack is launched every fourteen seconds! It isn’t surprising to note that over 80% of all data breaches in 2019 resulted from password hacks. The answer to overcoming these vulnerabilities is dual authentication or two-factor authentication (2FA).
Understanding Dual Authentication AndMFA (Multi-Factor Authentication)
Having acknowledged the dire need to protect users’ passwords from malicious actors, cyber experts enabled dual authentication for online accounts. In traditional access methods, one could type in their username and password and access their account just like that. However, since malicious actors today have innovative techniques and methodologies to steal or guess passwords, dual authentication has become necessary.
In dual authentication, you cannot access an account by merely typing in the password. The system sends a message to the user’s device, like a mobile phone, that the user must acknowledge. Usually, an OTP (One-Time Password) is sent to the mobile, which the user has to enter in a designated box on the screen of the terminal where they have entered the password. Thus, even if a malicious intruder manages to get the user’s password and type it in the password field, they still can’t access the user’s account; they will not have the code that was sent to the user’s device. Dual authentication or two-factor authentication (2FA) is known by that name as it involves two factors for authentication – a password and an OTP code in the example here. It is a subset of multi-factor authentication (MFA), which can even have more than two verification points. Dual authentication performs the following functions:
- It provides a double-layered (or multi-layered in MFA) shield against cyber threats by allowing users to verify themselves in more than one way.
- It only allows access after verifying all the authentication factors. Even if a malicious actor steals a password, he/she still won’t have access to files. That’s because access is granted only upon verifying user credentials through either a possession factor (a security token, cellphone, ID card, or a smartphone app) or an inherence factor (facial or voice recognition).
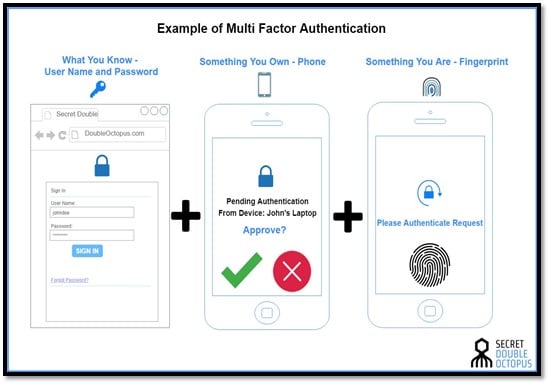
Dual authentication can be implemented in a variety of permutations and combinations with factors like:
- An alphanumeric password (Something you know)
- A passcode sent on the registered mobile (Something you have)
- A fingerprint or facial, retina, or voice recognition (Something you are)
For Google Workspace users, Google provides the following dual authentication factors:
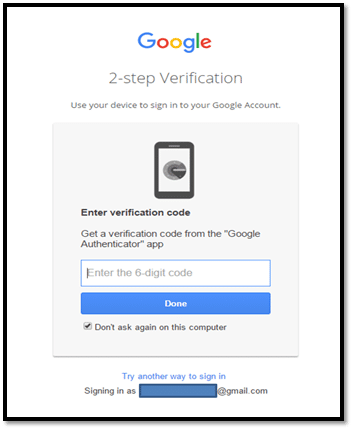
- A common way is to send a 2-step verification code to the user’s device via a text message or voice call.
- Security keys such as a hardware security key, Titan security key, and built-in security key are available for users. The device identifies a security key the moment users sign in, which then has to be connected to the device by USB, NFC, or Bluetooth.
- Sign-in prompts are another way where users can get a “Trying to sign in?” prompt on their devices, confirming which acts as the 2-step verification.
- Google even provides backup verification codes for 2-step verification, which can be printed beforehand if users need to access their accounts when they do not have their phone around.
How Does Dual Authentication Help Organizations Protect Their Information Assets?
A large number of people use the same password for all accounts. To make matters worse, malicious actors need less than six hours to decrypt 90% of passwords used by people, thanks to their advanced tools that enable them to test billions of passwords within seconds. In a scenario where attack ratios far exceed the adherence to password privacy protocols, dual authentication becomes a must for everyone. It is all the more applicable for organizations that regularly handle a vast expanse of customer and employee data.
Dual authentication helps organizations protect their information assets by providing much-needed assurance. It’s the era of mobility where employees carry the office on their mobile phones and laptops. In such cases, if a device gets lost and the password gets compromised, it becomes impossible to retrieve the confidential business files stored on it. But when dual authentication is enabled, an organization need not worry about such mishaps as it will make it near-impossible for the malicious actor to access the data on the device.
Do I Need Dual Authentication for My Business?
To answer whether a business needs dual authentication, one must look at the current statistics and attack patterns. Contrary to popular belief that passwords are the only tool required to keep users safe from attackers or that malicious actorsdon’t target individuals or small-scale businesses, the truth is that attacks can target just anyone on the web. The following subsections will show where organizations stand in the cybersecurity landscape and help decide whether one needs to implement dual authentication for one’s business.
- The Importance Of Dual Authentication
Every user must incorporate dual authentication for their primary email, financial accounts, and health records. Many people think that the process is tedious; why enter a pin code or wait for an OTP when unlocking the phone can help directly access the data? A survey reveals that 62% of small to mid-sized organizations do not enable MFA despite being aware of its significance. But in the unfortunate event of the phone getting stolen or compromised, it would provide the malicious actor with easy access to all personal or even business data. That’s why one can never negate the importance of dual authentication.
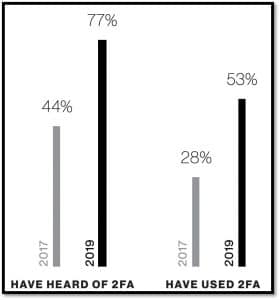
As a good sign, people have begun using 2FA much more in recent years than in the last decade. The following graph shows the increasing popularity and use of dual authentication.
- The Triumph Of Dual Authentication And MFA
Dual authentication is a must for those using online banking facilities, online shopping apps, email accounts, cloud storage, etc. The importance of 2FA is highlighted from a Thycotic survey that documented over250 malicious actors’ responses. These threat actors said that the two technologies they found cyber resilient and hard to penetrate are multi-factor a
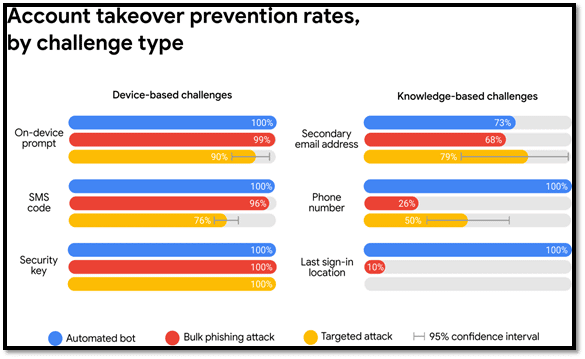
The above graph shows the extent to which MFA has been successful in managing various types of cyberattacks. It is proof of the efficacy of 2FA. 2FA-enabled SMS codes blocked almost all automated and phishing attacks. An impenetrable shield is created, which makes the malicious actors’ job difficult.
The 2018 Global Password Security Report states that only 45% of organizations use dual authentication as a security measure. While this figure marks an increase compared to the 24% use rate of 2FA in 2017, it is still not enough to protect businesses from malicious actors who are always looking for security loopholes.
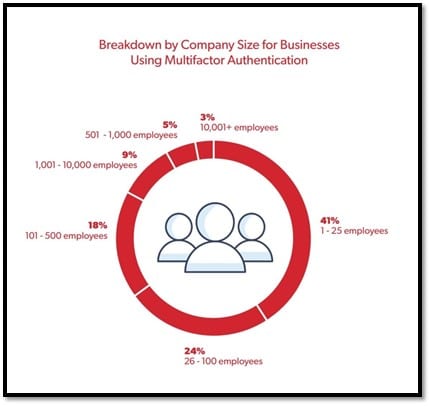
- The Higher Vulnerability Of SMEs
The general notion is that malicious actors only target large-scale businesses, but 31% of all cyberattacks have small and medium enterprises as their target. A KnowBe4 survey highlights some striking revelations about using dual authentication in large, vis-a-vis small and mid-sized enterprises. It says that a mere 38% of large organizations don’t use multi-factor authentication in contrast to 62% of small to mid-sized organizations. Similarly, there is a 9% difference in the implementation of password policies in large and small-scale enterprises.
- The Advantages Of Using Dual Authentication
Two-factor authentication facilitates a plethora of online activities that enable an organization to perform better. The following points justify why you must consider activating dual authentication for your business:
- Assurance: Enabling dual authentication allows IT administrators to be at peace, knowing that their computer systems and employees are less prone to unauthorized third-party access or compromise. Since two-factor authentication notifies administrators of every sign-in attempt, it becomes difficult for the malicious actors to infiltrate secure networks and extract data.
- Accessibility: Multi-factor authentication enables employees of businesses to work on the go. By promoting mobility and allowing employees to work from home, enterprises often unknowingly compromise on security. However, enabling dual authentication ensures easy accessibility to the organization’snetwork and promotes remote working by asking employees to log in after verifying their identity. The employees no longer need to confine themselves to one device or an office cubicle to do their work, as long as they take the two-factor test and provide the required security keys.
- Productivity: It is a direct outcome of the above factor of accessibility.Since2FA creates a safe working environment for everyone, business owners, employees, and IT teams can focus better on work without being concerned about security factors. Further, 2FA promotes remote working, which means that employees can work from any location, which also helps in increasing productivity.
- Reduction Of False Positives: Another reason to enable dual authentication is to reduce false positives or false security errors. It often gets overwhelming for businesses to handle the enormous number of login requests they receive from employees in a day. Naturally, there is a scope for threat actors to impersonate an employee and request login access. It has led to the doom of countless businesses in the past. However, with two-factor authentication, the error of false positives is reduced substantially as the login only happens when the users acknowledge the messages received by their devices. By removing unnecessary trouble of engaging resources to manage an attack that isn’t real, businesses save a lot of time, money, and energy.
- Cost-effectiveness: Dual authentication has time and again proved its efficacy in stopping a data breach attempt. Thus, it helps a business save millions of dollars, which would have otherwise been required to bear the cyberattack costs such as investigation charges, financial loss caused by a system failure, loss of goodwill, and immediate business opportunities. Furthermore, two-factor authentication ensures that IT experts do not have to spend time resetting passwords (approximately 20 minutes per password reset), saving valuable time and money for the business.
Thus, it is clear beyond doubt that dual authentication cannot be seen as an optional or additional feature anymore, but a primary cybersecurity necessity for individuals and organizations alike. The dangers lurking in today’s cybersecurity landscape are so varied and unpredictable that even two-factor authentication is not the single solution to all cyberattacks despite its many benefits. No security measure, for that matter, is the only or ideal solution to cyber threats. Just like the diverse forms of cyber-attacks, the cybersecurity measures are also many. It is always wise to use two or more cybersecurity strategies to ensure a safer online habitat for a business. One must incorporate dual authentication for their enterprise’s security without fail as it sees to it that no third parties access and misuse sensitive files.
Besides, healthy password habits must be adopted because it only takes a few minutes to break weak or recycled passwords. Healthy password habits include the use of alphanumeric and case sensitive characters. The passwords should be changed from time to time, and though tedious and hard to remember, efforts must be made never to use the same password for two accounts. Unique passwords are a must if cyberattacks aimed at account access are to be stopped.
Final Words
Cybersecurity is the concern of every business that has data as its primary asset. Since passwords are the only key that keeps all data secure, it is necessary to protect passwords and maintain password hygiene. A 2018 research suggests that over 2.5 billion accounts were infiltrated in 2018, which means that around 6.85 million accounts get compromised every day. Improving cybersecurity and protecting accounts can be done efficiently by enabling dual authentication as it acts as the primary shield from a password breach. Hence, every business and individual must consider enabling dual authentication for enhanced security.
BACK TO MAIN PAGE
