The COVID-19 Pandemic has exposed information infrastructure and security vulnerabilities in organizational defenses and has changed the threat landscape permanently. Organizations must create a post-pandemic cybersecurity strategy to survive and thrive in a new world.
COVID-19’s effect has been felt in many sections of the economy. Cybersecurity is one such sector that has witnessed massive changes. According to the FBI, cybercrime incidents have increased by over 600% since the beginning of the Pandemic. COVID-19 has exposed several vulnerabilities in organizational security. Organizations will now have to adopt a comprehensive new cybersecurity strategy for dealing with the changing environment and emerging threats. Emerging technologies such as Artificial Intelligence and Machine Learning (AI-ML) has wide cybersecurity applications and can help organizations safeguard themselves from existing and new threats. AI and data analytics can also be used to eliminate unnecessary log data and noise to let security analysts better understand their computing environment. AI solutions are capable of detecting malicious behavior patterns in network traffic.

What Will the Post-Pandemic Cybersecurity World Look Like?
The Post-pandemic world will see organizations and experts becoming more united in their fight against cybercrime. For instance, groups such as the COVID-19 Cyber Threat Coalition or CTC have already been established, and CTC has 3000 members. Such groups will share data to help prevent threats. It is also expected that organizations will place more emphasis on cybersecurity due to rising global awareness. Organizations must create their cyber plan to counter rapidly evolving threats. Consider the following statistics:
- Ransomware attacks alone will cost organizations $6 Trillion by 2021.
- 98% of attacks have some elements of social engineering, and remote workers are at risk
- Targeted users open phishing emails 30% of the time.
- Malicious links are clicked 12% of the time.
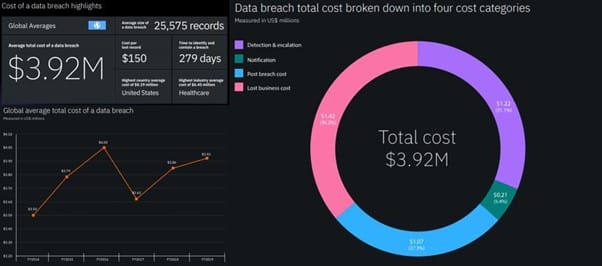
- A data breach costs organizations $3.92 million on average
Six Post-Pandemic Cybersecurity Strategies with Long-Term Benefits
Making a new cybersecurity strategy and implementation plan can provide several dividends for organizations. Each of these six methods will be an effective cybersecurity strategy – 2021 and beyond.
- Adopt a Cloud-Based Cybersecurity Strategy
The Pandemic led many organizations to shift to cloud technologies and benefit from seamless access to applications and data. However, remote access to cloud resources increases risks from data breaches, misconfiguration, insider threats, and so on.
The post-pandemic world will witness resources shifting towards data and data security in cloud platforms. While the cloud presents new challenges, it also provides several more benefits than traditional cybersecurity strategies, especially for cloud-based networks. Benefits of including cloud in a cybersecurity plan include:
- Real-Time Threat Detection
In traditional cybersecurity, network monitoring is performed at regularly scheduled intervals. Unidentified threats can thus cause significant damages.
In contrast, a cloud-based cybersecurity strategy allows for faster detection of threats such as malware and viruses. It also enables real-time network monitoring, threat identification, and containment.
- Automatic Security Updates
Upgrades and updates take longer when traditional cybersecurity mechanisms are used. The reduced speed is due to each device receiving updates individually. Some devices may even be missed, thus risking the entire network.
However, a cybersecurity strategy based on the cloud allows all devices to remain updated with the latest security updates continually. All upgrades are instantly installed in the whole network and end-devices leaving no vulnerabilities for adversaries to exploit.
- Mobile Device Security
Healthcare organizations cite insecure mobile devices as the third-largest threat. Devices such as laptops can pose a significant risk to network infrastructure as they are used in diverse environments that may or may not be secure. A cloud-based strategy allows in-depth monitoring of mobile devices for easy localization and containment of security threats. It also enables admins to place controls for restricting mobile access to specific areas of the network.
- Build Trust Internally and Externally
Trust building and communication is an essential element in cybersecurity. The board, top-level executives, and staff need trust to cooperate and synergize for adapting to the new scenarios. The focuses given below will provide significant dividends in the post-pandemic world:
- Internal Trust Building
Security must be integrated into all levels of the organization to creating an internal environment of trust. Executives must merge both work and security strategies. As new technologies are strategically adopted, cybersecurity must be a significant partner. CISOs should be involved in selecting new technologies and enjoy increased communication with the board and C-Suite.
- Trust Building With Clients
The shift to online platforms for much of an organization’s daily work has led to clients expecting a greater emphasis on cybersecurity and data security. Organizations need to visibly show that their cybersecurity safeguards, data storage, and collection meet demands. Data security and privacy are among the essential elements of an organization’s ESG agenda. They can win trust by striving to exceed the minimum requirements of regulators.
- Developing Trust With Regulators
A large part of cybersecurity is compliance, and regulators are increasingly demanding proactivity and transparency. An organization’s cybersecurity team, public relations, and legal teams should communicate to regulators that its data collection and storage methods exceed expectations for safeguarding client and employee privacy.
- Consider a Decentralized Cybersecurity Approach
Due to millions of employees now working from home, adversaries have started shifting their focus from the enterprise to remote workers. Decentralized cybersecurity is a feasible strategy to meet this novel challenge.
Decentralized cybersecurity involves moving security controls to data sources like remote employees and firewalls based on endpoints. Decentralized data loss protection and digital rights management are also included. Benefits of decentralized cybersecurity include:
- No Single Points of Failure
In a decentralized system, services and applications function using individual computing devices and nodes on distributed networks. Thus, centralized servers are rendered unnecessary, which leads to greater resilience in the entire network by removing single points of failure.
- Enhances Access to Information and Talent
Decentralization allows organizations access to information and talent that they might not possess otherwise. It enables them to benefit from real-time threat intelligence and data shared by security teams and security operations center analysts worldwide.
- Greater Data Security
Decentralization can help organizations improve data security. In most situations, adversaries look for a single source containing information. They use technologies such as spear phishing to access such sources of data. Decentralize attempts to mitigate this problem by removing databases that contain aggregated confidential data.
- Alignment of Security And Organizational Goals
In a decentralized IT security approach, every organizational unit assumes responsibility for developing its standards and policies. Decentralized security models lead to units readily embracing security programs, assigning necessary resources, and implementing them. As units act individually, they gain more efficiency in implementing policy changes and conducting incident investigations. The security policies are also more likely to be aligned with the unit’s organizational goals.
- Embrace Emerging Technologies
Threats in the cyber arena are evolving at an unprecedented rate. Organizations must embrace emerging technologies like artificial intelligence and machine learning to combat the growing risks.
- Artificial Intelligence
Artificial Intelligence and Machine Learning (AI-ML) algorithms can improve cybersecurity posture through intelligent code analysis of large amounts of data. It can also assist in developing enhanced recovery and prevention strategies. Several providers have started using artificial intelligence in their offerings. The security organization Darktrace states that their ML technology identified more than sixty thousand formerly unknown threats on five thousand networks, including internal attacks, ransomware, and zero-day exploits.
The SANS institute states that spear-phishing is behind 95% of all attacks on the networks of enterprises. Phishing is becoming increasingly dangerous and efficient. Next-generation attacks are being carried out using SMS (SMSishing), voice calls (Vishing), online advertising, and social media. AI phishing detection technologies provide critical insight, intelligence, and detection of such emergent threats.
- Biometric Authentication
User access controls have traditionally been limited to two-factor authentication. Such methods rely on the “Something user has” (Username) and “Something user knows” (Password) method. Passwords are often easy to breach, as seen in the Solar Winds hacking.
Adversaries thus see employees as a weak link, and cyberattacks are increasingly being directed at individuals. Advanced biometric solutions such as Iris scanning, fingerprint scanning, voice, and facial recognition technologies focus on “who user is” and are much harder to impersonate.
- Virtual Desktops
Tele-working is likely to remain a norm for several organizations in the future. As such, adopting virtual desktops can bring security benefits. Virtual desktops allow IT teams to control input-output devices, applications, and software by emulating computer systems. Such control points are essential when dealing with remote workers who operate outside the organization’s networks’ safety. Virtual desktops help professionals enforce standards for the management of data. They could become a necessity to meet stringent compliance and regulation criteria.
- Human-Centric Cybersecurity Strategy
The people of an organization are often its most vulnerable point. Pre-COIVD data showed that Human error is the cause of around 90% of all data breaches. The added uncertainty of using new technologies will lead to a crisis.
A human-centric cybersecurity approach that emphasizes education will safeguard organizations where they are vulnerable.
Some ways to improve cybersecurity are:
- Formal Training Program
Cybersecurity Training Programs are a direct and straightforward way to improve awareness in an organization. They leave employees little doubt that cybersecurity is essential to the larger organization and makes them aware of what practices to follow. Regular and active training of employees against phishing and social engineering can prevent devastating attacks.
- Test Employee Awareness
Actively testing employee awareness is necessary to reveal security gaps and ensure that employees internalize lessons learned during formal training programs. Such testing can be anything ranging from assessments after training programs to fake phishing attacks conducted during red-team blue-team exercises.
- Highlight and Share Major Cybersecurity Incidents
Highlighting significant incidents when they occur, either in meetings or newsletters, is another way to raise awareness about cybersecurity risks. The incidents should be discussed along with the backstory as to what lead to the attack. Such discussions highlight why following best practices in cybersecurity is a good idea.
- Use SIEM and DLP
Security Information and Event Management (SIEM) analyzes information from an organization’s network infrastructure. Organizations use SIEM to protect sensitive data and collect proof that they are doing so for compliance requirements.
SIEM works best when used with other tools such as Data Loss Prevention (DLP) and Identity and Access Management (IAM). It gathers information from the firewalls of security tools and IAM protocols.
The benefits of SIEM are given below:
- Management of Logs
Remote work has increased the number of endpoints that need to be monitored and secured. Log management using SIEM lets organizations ensure visibility over endpoints and the activities of remote workers. SIEM does not let security events go unnoticed but logs them for analysis.
- Compliance
Remote work has made monitoring data to ensure that it remains compliant a challenge. SIEM helps organizations automatically gather data for compliance reporting and makes compliance simple. Solutions also provide automated reports, saving IT professionals resources and time.
- Preventing Data Loss
DLP tools are used to prevent breaches that occur due to employee error. They monitor data at rest, in use, or in transit to significantly help stop accidental exposure of sensitive data in a network’s devices. Such tools make it so that confidential data cannot be sent through emails without the security team’s permission. Several breaches start with adversaries accessing a misconfigured or unknown cloud database. DLP tools mitigate such risks by preventing unauthorized cloud or external backups.
Conclusion
The Pandemic is a historical event that has changed the world forever, and organizations must adopt new strategies to survive and thrive in the new scenario. Embracing technologies such as AI-ML, SIEM, decentralization, and cloud cybersecurity in a new IT security plan can help. At the same time, they must build trust both internally and externally and raise employee cybersecurity awareness through training. At the same time, decentralization can help address the workforce shortage in an industry faced with ever more sophisticated threats and increasing attack surfaces. Organizations can thus accelerate the detection and mitigation of novel threats. An analyst could flag suspicious emails and files by sharing intelligence, which would then be automatically distributed to other analysts on the network. Such activities would reduce the time necessary to research new threats and enhance their capacity to respond to attacks.
BACK TO MAIN PAGE

