Cyberattacks have become more common and frequent in today’s times. Therefore, it has become necessary for businesses to have stringent cybersecurity policies to thwart such malicious attacks and protect their confidential data from falling into the wrong hands.
When it comes to cyberattacks, businesses, especially SMEs, usually have the “It will not happen to me” mentality. However, it is not so because every business, big or small, is at equal risk from cybersecurity breaches. Malicious attacks come unannounced. Hence, one never knows when their organization would become a victim. Therefore, businesses should be well-prepared to face any risk at any time. Here is an examination of how businesses can protect against cyberattacks, irrespective of the budget.

Some Key Statistics On Cybersecurity Attacks
Before thinking of ways to thwart cyber threats, it is good to have an overall picture of cyber-attacks’ types and magnitudes. Here are some critical statistics and forecasts concerning cybersecurity breaches that cannot be ignored.
- By the end of 2021, the frequency of ransomware attacks would be around one in every 11 seconds1.
- Global ransomware damage costs will reach the $20 billion mark by 20211.
- Malicious actors prefer using the email route for delivering malware in 94% of the cases, according to a Verizon report.
- Phishing attacks accounted for more than 80% of reported cybersecurity breach incidents.
- 18% of small and medium businesses list cybersecurity as their least priority.
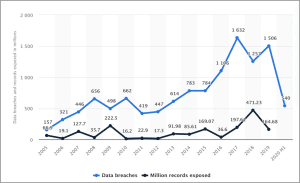
Data breaches have increased exponentially in the US and globally over the years. Here is a graph of the annual number of data breaches and exposed records in the US from 2005 to the first half of 2020.
What Are Some Of The Most Common Cyberattacks, And How Do They Take Place?
Before discussing some of the common cyberattacks3, let us first understand the term ‘cyber-attack’ itself. A cyberattack happens when a malicious actor attempts unauthorized access into any IT system with the intention of theft, disruption, extortion, or other nefarious motives. Cyberattacks not only happen through external malicious actors but also internally from organization members themselves. Here are some common cyberattacks that take place in the industry and their modus operandi.
- Ransomware – Here, a malicious actor infiltrates enterprise networks and install malware. It restricts access to the user to their data, usually by encrypting it. The malicious actor demands a ransom to deliver the code/decryption key that grants access to the data. The ransom is usually demanded in cryptocurrency.
- Phishing – Phishing is by far the most common of cyberattacks. The cyber-attacker attempts to trick an unsuspecting victim into parting with confidential information such as credit card info, passwords, or intellectual property. These attacks originate through an innocuous-looking email pretending to originate from a reliable source. The email contains malicious attachments or links that the unsuspecting victim opens or clicks, triggering malware download or redirection to a fake website, respectively.
- Man-In-The-Middle (MITM) Attack – This form of cyber-attack involves the attacker intercepting communication between two parties and spying on critical info. The malicious actor can also alter the communication between the two parties.
- Distributed Denial-of-Service (DDoS) Attacks – The cyberattacker floods the target server with excess traffic to disrupt and bring down the target. Since multiple terminals generate malicious traffic, it is usually impossible to stop it with commonly applied methods.
- Business Email Compromise (BEC) – Such attacks have gained prominence comparatively recently. Here, the attacker targets specific users by impersonating those in top management positions like the organization’s CEO and trick the unsuspecting target into transferring money into the threat actor’s account.
There are also other forms of cybersecurity attacks like SQL injections, Zero-day exploits, DNS tunneling, Cryptojacking, XSS attacks, password attacks, IoT-based attacks, and AI attacks. All these attacks are spine-breaking and can pose a financial risk to the organization. Hence, every business enterprise should have robust cybersecurity strategies in place to manage these risks.
How Can Organizations Protect Their Information Assets Against Cyberattacks With Or Without A Budget?
With all business organizations functioning online, there is a corresponding rise in cybersecurity attacks on business enterprise networks. Hence, every organization should do everything they can to protect their information assets against cyberattacks. Let us discuss how organizations should approach the problem with and without a budget.
With Budget Support
Specialized cybersecurity strategies come at a significant price. Businesses with an adequate financial backup should have an earmarked budget for having such a system in place. Here are some of those strategies.
-
Dedicated Job Role Specific Training
Ideally, every employee who touches a computer should receive adequate cybersecurity training. Every business organization usually has an in-house team to train employees on matters concerning cybersecurity. However, it is not sufficient because malicious actors invent novel methods to access enterprise networks. As the technology keeps improving, so do them as they explore innovative ways to launch cyberattacks. Hence, businesses should prepare themselves to be a step ahead of malicious actors. One way to do so is to impart dedicated job-role specific training to employees5.
Organizations have specialized posts for managing cybersecurity issues. For example, a Security Administrator is responsible for managing all IT-related security and safety issues within the organization. Such a designation requires a person to have updated knowledge of cybersecurity. Hence, the organization should encourage the employee to go for specific job-role training like learning the same advanced hacking methods and techniques leveraged by malicious actors. They can also keep themselves updated with tools and tactics to manage cybersecurity risks and identify the latest types of cyber threats. They should have the capability to analyze cybersecurity intelligence and handle cyber incidents as they occur.
Similarly, a Security Analyst should develop penetration testing skills to identify IT-system vulnerabilities and effective remediation techniques for such exposures. The Security Analyst should also understand legal and compliance requirements and update themselves to analyze, report, and communicate results.
There are other specific job-roles such as the Security Engineer and the Security Manager with particular responsibilities. The organizations should allot a dedicated budget to impart job-role-specific training to make professionals remain updated and some steps ahead of the malicious actor.
-
Leveraging AI-ML-based Cybersecurity Tools
Today, AI and ML have become common in organizations worldwide. Everyone today uses AI and ML to make life easier, but there is an unexplored dark side to it, as well. Cyber adversaries have tapped this resource and launched AI/ML-based cyberattacks. A widespread software tool is DeepLocker6, a new generation malware that remains undetected until it reaches the target. This malware uses AI models to identify its targets using common indicators like voice recognition, facial recognition, and geolocation.
Organizations should fight fire with fire. It is better to use AI/ML-based cybersecurity tools7 to manage and thwart such AI/ML-based cyberattacks. Some of the best tools that businesses can leverage include the following.
- Symantec’s Targeted Attack Analytics – The TAA tool helps uncover stealthy and targeted attacks. It was used successfully to counter the Dragonfly 2.0 attack. It detects suspicious activity in the individual endpoints and assesses the information to determine whether the actions indicate hidden malicious activity.
- Darktrace Antigena – This AI-based tool identifies suspicious activity and responds to it in real-time. It uses ML to regulate user and machine access to the internet without disrupting regular business activity.
- IBM QRadar Advisor – This cybersecurity tool investigates threat incidents by mining local data. It assesses the threats that have bypassed layered defenses.
-
Red Teaming (Hiring Third-Party Assessor)
At times, looking at cybersecurity issues from the malicious actor’s perspective can help find solutions. Such a practice is known as Red Teaming in cybersecurity circles. The term originated in the armed forces. One of the earliest implementations of this security measure is ethical hacking.
However, the official definition of Red Teaming is the practice of challenging plans, systems, policies, and assumptions by adopting an adversarial approach. Generally, it involves hiring a third-party assessor that uses strategies to encourage an outsider perspective. Some of the red teaming techniques8 an organization can employ are the following.
- Think-Write-Share – Here, the group members generate ideas, write them, and share them with others. It helps individuals to retain their perspectives rather than getting influenced by those of others.
- Devil’s Advocacy – This method envisages people developing ideas and counter-ideas to present the most compelling arguments against the prevailing concepts. It is more like playing the Devil’s Advocate in a debate.
- Be your worst enemy – This process involves taking an adversarial approach and thinking like an opponent. It gives a fresh external perspective of the problem and assists in finding apt solutions.
-
Independent Third-Party Review/Audit/Control Assessment
Organizations should have a check on their operations by employing independent third-party reviews or audits9. Such control assessment exercises do not eliminate the risk of cyberattacks but ensure that the business has cybersecurity measures in place. It helps in identifying the vulnerabilities and loopholes of the organization’s enterprise information network. Thus, it helps in taking preventive and precautionary measures in advance to mitigate cybersecurity risks.
A third-party control assessment offers an independent perspective that is not clouded by internal influences. Thus, businesses get an impartial opinion of the cybersecurity measures prevailing in the organization. It can help them ramp up their defenses without affecting the core business in any way.
Without Budget
While various state-of-the-art cybersecurity strategies cost a considerable amount, there are also some measures where the organization need not invest much. Here are such examples.
-
Creating Employee Awareness
In matters concerning cybersecurity, an organization is only as strong as its weakest employee. Hence, every employee should be cyber-vigilant to prevent data breaches and other cyberattacks from occurring. Organizations should impart regular cybersecurity training to their employees to create the required awareness.
Every employee in the organization should know the following.
- How to use emails securely for business and personal use
- How to treat confidential business information at the office or home without jeopardizing the organization’s interests
- The immediate steps to take if a cybersecurity incident occurs
Organizations should ensure that every employee is aware of phishing and BEC risks that can compromise confidential data, leading to business and financial losses. Every new employee should learn to protect data. Organizations can use internal information-sharing mechanisms like newsletters and provide ongoing training to reinforce cybersecurity culture.
-
Regularly Reviewing And Strengthening Cybersecurity Policies
Every organization should have an effective cybersecurity policy. Besides, they should ensure updating and reviewing the policy from time to time. As technology advances, so do the malicious actors.
The cybersecurity demands keep changing with time. Therefore, businesses should keep strengthening their policies by reviewing the existing clauses and improving on them. They should also ensure sharing the revised cybersecurity policies with each employee to increase employee awareness and strengthen the organization’s cybersecurity posture.
-
Building A Cybersecurity-Aware Culture
Each employee should understand that cybersecurity is everyone’s responsibility and not of the IT security team alone. The IT team is always available to guide the employees, but the frontline employees are the ones who have to keep the policies established.
One slip from a front desk employee is enough for a significant data breach to occur. Hence, cyber vigilance is critical for the organization. Every employee, right from the CEO to the most junior employee, should consider cybersecurity as an inherent responsibility and develop a cyber security-aware culture in the organization.
Final Words
Cyber threats are real and can occur at any time. Organizations have to be vigilant to prevent them from occurring and creating havoc with the enterprise network. Business entities should ensure maintaining the most robust cybersecurity strategies in place. Perhaps, the best way to ensure cyber vigilance (for those without a significant budget) is to develop a cybersecurity awareness culture. Providing adequate training to employees also helps enhance their awareness levels. Simultaneously, the organization should employ the requisite security tools to prevent cyber adversaries from gaining the upper hand. Ideally, the enterprise should have a distinct cybersecurity budget to take care of the expenses in setting up a robust cybersecurity strategy.
BACK TO MAIN PAGE
