Cloud computing services entered the Information Technology landscape recently but have spread fast like wildfire. While it offers many scalabilities, cost-effectiveness, and conveniences for large and small organizations, hidden beneath its outward appearance are high-security vulnerabilities and risks associated with virtualization and multitenancy.
The Cloud computing concept has eased many a burden for a large number of establishments, such as resource scalability, availability, and cost-effectiveness. Many organizations have been migrating their workload to the Cloud at a rapid pace. However, a pestering fear remains – data privacy and security. Many Cloud users are still grappling with the idea of how secure the Cloud is? Can they move their customer’s personal data in the Cloud? Will they still comply with the applicable regulations? How about the audit in a cloud environment? And this fear is entirely justifiable too. Data security in cloud computing is a significant concern that has acted as a roadblock for most customers.
The Cloud does offer its clientele a range of positives that can be leveraged to their advantage. However, the question of security always remains. Information security framework, standards, and guidelines are still not fully developed, and hence senior management must do the necessary due care and due diligence regarding cybersecurity issues and decisions. This will ensure that the confidentiality, integrity, and availability of the enterprise information assets are always protected.

What Is Cloud?
A Cloud service may be described as one that provides its consumers on-demand software and hardware functionalities through the Internet. That would mean that one could easily avail hardware and software resources such as storage and computing power whenever needed using online connectivity. One does not need to have an in-house arrangement for such resources and infrastructure. The Cloud services provider will store the requisite hardware and software in their data centers. They purchase, operate, and maintain such resources so that users do not need to buy and install, or even support them.
These Cloud services are used on a subscription basis. It depends on the usage, and the subscriber can scale the usage up or down as per demand. The providers would bill accordingly. With many Cloud management tools in the market, the entire customer management is done without direct human interaction. Hence, the whole process is automated.
While Cloud services use the Internet as a means, it is not synonymous with the web. A good example would be that of Google Search and Gmail. While Google Search uses the Internet’s power to fetch the information one is looking for, Gmail stores all the data in the Cloud. It is software not installed on individual computers but in a separate location where it reproduces the relevant IPs’ information. Another example of a similar service that stores all the data in the Cloud is Google Docs.
For large organizations, Cloud storage often replaces the computer hard drives, which has its limitations. These organizations pay a timely subscription, and all they have to take care of is the subscription bill.
With Cloud services becoming the buzz ringing hard in the technological landscape, all organizations need to pay serious attention to the negatives of the concept, too, as much as its positives.
How Secure Is The Cloud?
The following graph shows the security concern of users subscribed to Cloud computing services. As is evident, the subscribers’ largest fears are about data loss or leakage and a breach of privacy/confidentiality.
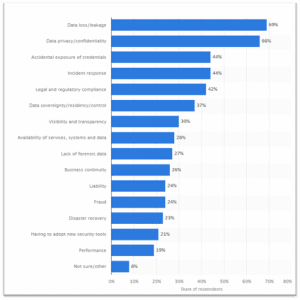
With the tech world moving towards the Cloud faster, questioning the architecture’s security is legitimate. Since users would store enormous amounts of data in the Cloud, any loss could lead to a catastrophe for the organization’s information assets or the individual’s PII (Personally Identifiable Information).
A current survey suggested that almost 94% of organizations had concerns regarding the security of the Cloud. When asked specifically what the security concerns were, the following was the breakup provided:
- 68% were concerned about misconfiguration of settings, which was considered a big reason for data breaches.
- 58% were concerned about unauthorized access
- 50% thought that malicious agents could hijack their accounts.
These statistics are prima facie to the fact that although Cloud provides enough security to the data stored within, vulnerabilities and threats are lurking. These specific threats that make companies wary of Cloud storage and computing are discussed in detail below.
The Biggest Threats Of The Cloud
- Misconfiguration
It is easily the greatest nightmare faced by any organization, as stated earlier. Misconfiguration of the Cloud settings primarily emanates out of a few things, the most dominant ones being:
- Easy Accessibility
- Lack of control over the Cloud Infrastructure
Cloud is designed to be non-cumbersome. It is the USP (Unique Selling Proposition) of the architecture and its primary marketing point. Cloud storage is supposed to be comfortable as a breeze and without complexities and complications. It often gives rise to accessibility issues. Being easily usable allows anyone and everyone to become a part of it. For large corporations storing tons of data, this is a concern. Because of the Cloud’s design, it is difficult for organizations to have full access control.
There are many Cloud storage providers in the market, each providing competitive services. It is expected that a single organization has its services shared by multiple vendors. It leads to a peculiar situation for the consumer. Firstly, they do not have any control over or visual engagement with the infrastructure. And secondly, the security being provided becomes the responsibility of the vendor alone. This lack of security oversight and the spread of the services across multiples Cloud Service Providers may lead to misconfiguration.
- Access Management Issues
The Cloud is designed for easy access and hence uses the Internet for entry. While it solves the issue related to accessibility, it also creates an easy pathway for the malicious actors who want to steal or misappropriate data. Unauthorized access is one of the biggest challenges in the virtual world. With the continuing rise of cyberthreats such as phishing, malware, and ransomware, data security teams and IT Security specialists are always on their toes to counter such attacks. The strength of the Cloud, in this case, turns out to be its Achilles Heel.
- Account Compromise
Weak passwords have been the bane for humanity for a long time. Remembering complicated passwords being a liability has led most passwords to be easily guessable and vulnerable to misuse. The hijacking of passwords is one of the most severe methods of data-stealing. Threat actors could also steal passwords through phishing. They may resort to impersonation and confuse an employee to gain access to data. Another concern that compounds the severity of the issue is that most organizations cannot identify these threats. Cloud Infrastructure cannot put into place mechanisms that may deter such occurrences entirely, though the near future looks bright from the security point of view.
- Less Or No Visibility
The advantage of Cloud computing is that no hardware or software would have to be installed on the user’s computer. The entire information set would be fetched from the vendor data center and used as per the subscription model. The onus of security, purchase, maintenance, and installation lies with the Cloud Service Provider. While this is a great way to outsource a significant chunk of resourcing and helps bring down infrastructural costs, the risk lies in the fact that the user has no visibility over the data that has been stored. Given the way the Cloud works and its easy accessibility, IT Security teams are always on tenterhooks. This lack of visibility limits the organization’s capacity to monitor the data effectively.
- Cyberattacks
The virtual world is a veritable battlefield. With advancements in technology, the increased sophistication of cyberattacks has left many an organization bloodied and bruised. The Cloud’s easy accessibility through the Internet makes cyberattacks easier. The risk is many times more if it is weakly secured. Another fact that aggravates a cyberattack’s consequences is that multiple organizations use the same Cloud infrastructure, making it easy for malicious actors to perpetrate their crimes.
- DDoS Attacks
Distributed Denial Of Service or DDoS is another concern of most organizations. Many organizations have customer-facing applications that are critical to the continuity of services. A Denial of Services attack would lead to these functionalities being rendered useless, and as a result, the business would suffer. Most DDOS attacks are linked to ransomware, whereby malicious actors ask for a ransom to reinstate the services. It is one of the techniques used most by malicious actors and cyber perpetrators. There have been numerous incidents that have led to Cloud Service Providers creating additional firewalls around their services. Even the Cloud architecture is undergoing significant transformations to counter DDOS attacks.
Other Crucial Concerns Organizations Have To Face Pertaining To The Cloud
- Complex Architecture
Cloud storage and computing is a relatively new discipline, and it is still in an evolutionary stage. The technological complexities increasing by the day are among the concerns that organizations face because of a fundamental flaw: Lack of Human Resources.
Cloud Infrastructure and managing resources require adequate knowledge. The existing staff may not be able to provide all-round support to their employers concerning security. It puts a strain on the trained resources. While they may be able to integrate and manage, encryption and Cloud management are problematic areas requiring sustained focus. Adding to this trouble would be the ever-changing threat scenarios, policies, and legalities. All these complications have a high probability of creating gaps in the security framework. Malicious actors are well aware of the changing dynamics of Cloud computing and the difficulties it brings along. They are always vigilant, looking out for the smallest chink in the armor, and will spare no time in pouncing on it.
- Lost Data
Data stored within the Cloud can be lost for reasons other than cyberattacks. There can be accidental deletion of data or natural catastrophe hitting the data center. There is also the curious case of customers losing the encryption key used to encrypt their data. All these losses are usually not accepted by the service provider. However, one area of business that has benefitted from this is the data recovery market. Having stored sensitive data in the Cloud, every organization will have signed up for data recovery in the event of data loss. Some contracts stipulate such a service and must be looked into when the organization signs up for the Cloud service.
- Lack of Due Diligence
While transferring services and data to the Cloud, most organizations fail to look into the smaller details. It may be born out of a lack of awareness and knowledge. There are cases when the decision to move to Cloud has solely been based on the price advantage and nothing else. The most important thing to consider while dealing with CSPs or Cloud Service Providers is the security measures taken, the response time in the event of an incident, and the data recovery capabilities. While cost is indeed an essential part of any business negotiation, it is imperative to look into the other aspects, too, since any data loss would lead to a tremendous financial and reputational loss.
Two Must-know Cloud Vulnerabilities For Every Security Manager
The Cloud is a relatively new concept with a large market already under its belt. The rapid rate of growth has also been nothing short of spectacular. However, it has also amplified the vulnerabilities that otherwise lay hidden behind the façade of it being a tech marvel.
- In-system Exploitation
The Cloud is home to multiple organizations sharing space. With easy entry and Internet led accessibility, it provides just the right doorway for malicious actors to exploit the service provider’s in-system vulnerabilities. Once inside, they will be able to use one data against another and control the environment. Multi-tenancy, while often lauded as a cost-effective means to store information, does have a pitfall. It increases the surface area of attack, and the probability of successful hits is high.
- Compromised APIs
Users and CSPs interact through a set of APIs that have the same vulnerability as any other software. Organizations use these APIs to interact with, monitor and manage their data to a certain extent. These APIs are also accessible through the Internet and could remain open to malicious interventions.
Final Words
Every system evolves, and so will Cloud computing. Like every tech faculty, the Cloud is vulnerable to sustained efforts by malicious forces such as advanced persistent threats or APTS. Only dedicated efforts will be able to eliminate these threats and vulnerabilities once greater focus and resources will be poured into it, which is undoubtedly being taken as a priority by organizations worldwide. Despite all the challenges surrounding the transformation, the Cloud has become an indispensable means to conduct business in today’s fast world, and we can surely expect many more revolutionary evolutions in Cloud technology in years to come.
BACK TO MAIN PAGE
