Since the arrival of Covid-19, many employees have been working from the comfort of their homes and delivering results quite magnificently. However, remote work does have its drawbacks, which must be taken care of by organizations.
With the unrelenting rise of Covid-19 cases, the chances of returning to work seem to be fading for many organizations. Working from home has thus become the new normal. Working remotely is not new; even before Covid-19, many organizations had been accomplishing various projects with employees located in different locations for carrying out their myriad tasks. Irrespective of whether it is due to Covid-19 or not, a distributed remote workforce comes with its host of vulnerabilities. Organizations have to direct serious attention to the matter to avoid huge losses and unwanted complications.
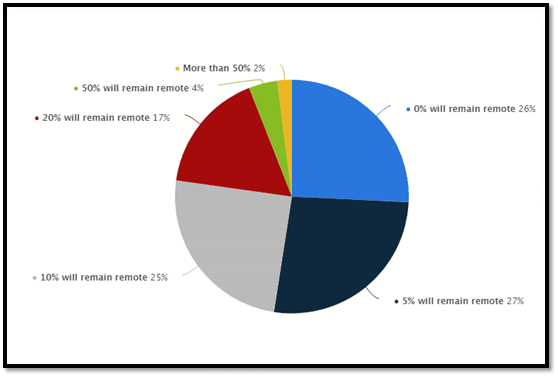
What percentage of your workforce will remain permanently remote post-COVID who were not remote before COVID?
Source: Statista
What Are The Prerequisites For Working Remotely?
Working remotely depends on organizational policies. If it decides that the employees have to work remotely, specific prerequisites need to be fulfilled. A critical criterion is having a fast and smooth internet connection with the employee at the location they are stationed for work. Without good net connectivity, the entire premise of working remotely will fail.
Efficient management is also required to handle all the remote employees and coordinate work effectively to accomplish goals. An effective communication setup is necessary to get the team going at the required pace without any obstacles. The enterprise must leverage text, audio, and video communication technologies optimally to update the projects’ progress, provide instructions, and impart training.
Keeping digital information and systems secure, especially at the remote work location, is yet another requirement. There are a few more criteria to follow to maintain a remote work setup efficient and safe.
What Does A “Distributed Team” Mean?
A distributed team is one whose working members don’t work physically together in one place. Instead, they will be located in different locations. They could be working wholly from their homes or other remote locations, i.e., a location other than the usual workplace. Many organizations have distributed groups spread worldwide, working from their respective areas and delivering results. Numerous organizations have remote working positions for their employees. It may so happen that part of the team works from the premises while the rest works remotely.
What Are The Pitfalls Of Working Remotely?
While working remotely may become part of an effective Business Continuity Plan, especially in the pandemic, it has its drawbacks. The following are the threats to WFH:
 (Image Source: Pixabay)
(Image Source: Pixabay)
- Phishing
It is one of the most prevalent cyber attacks that has remained a menace for a long time. Malicious actors use phishing to gain access to secured networks, and they wreak havoc once they penetrate the system. From stealing data to planting malware, the malicious actors’ activities are varied. Phishing is not just a threat to organizations but an equal threat to remotely distributed teams.
- Covid-19 Scams
It is the latest in the long line of threats that organizations must look into seriously. Threat actors are trying to gain maximum mileage out of the raging pandemic. There have been umpteen scam donation campaigns in the name of Covid-19 Charities. Many of these websites impersonate the real ones and fool visitors into believing their ruse. All these websites have links that take the user to another page that collects their credentials and banking details. Users must be aware of such con projects. The Covid-19 scam has also been extended to vaccine programs, making people believe that they could receive the vaccine first by paying a certain amount.
- Malware
Malicious actors understand the vulnerabilities of systems through which employees work remotely. One of the acts they participate in is loading malware into the system. Once the malware is in the network, it will start collecting sensitive data and saving them in remote servers. Malware has the capability of disrupting large networks and causing harm to organizations, financially and reputation-wise. Malware can remain undetected in systems for an extended period before being discovered. Hence, employees need to be aware of links and websites that can dupe them.
- Malicious Apps
Much like websites, there are malicious apps that do the same thing. They collect data from users and may use it for a variety of unlawful purposes. For instance, Malicious Azure apps are some of the biggest threats and are responsible for misappropriating user data.
- Man in the Middle (MITM) Attack
In this form of attack, malicious actors can intercept a communication path in a network. They can position themselves between a sender and a recipient and access the communication between them. They may delete or alter the messages passed while the sender or the receiver remains unaware of what’s happening. The malicious actors can plant malware into the system or utilize the accessibility for other malicious purposes.
- Insider Attacks
Employees may download and save work on unsecured devices and start working on them from those devices. It will create a scenario where the organization may not have adequate control of the files and the situation. There are many other chances also for insider attacks. For instance, an employee can forget or lose an official device in a public place, exposing confidential and critical data to anyone. A disgruntled employee divulging information to a malicious actor is yet another possibility. Such attacks are one of the biggest threats for IT Security teams. They are more focused on attacks emanating from external sources than internal ones. Insider attacks are some of the most difficult ones to track and overcome.
Strategies to Secure The Distributed Workforce
Since the mounting challenges that remote work throws can be catastrophic, organizations must always stay a step ahead in handling them. Here are the usual strategies that organizations need to implement to prevent their data from falling into the wrong hands.
- Setting up a VPN
All the paraphernalia related to data security that organizations invest in is onsite. The office infrastructure is used to create a state-of-the-art firewall. Even when employees work remotely, they are provided with official devices with configured tools to assist them. Employees log into the remote systems and go about doing their official work. The connections are made to the servers securely, through secured routers set behind the network’s secured perimeter.
What will happen if the employee accesses the same network from a remote location using an unsecured device and an unsecured Wi-Fi connection? The IT Security team cannot always secure personal devices, and it then becomes a challenge for them to prevent cyber-attacks. These are potential risks for malware planting and other cyber attacks. Open networks are easy to access for malicious actors who use them to gain entry to the user device. With the absence of a protective layer, the user will not identify the threat and carry on with the task as usual. The threat actors thrive in such cloaks of invisibility.
Under these circumstances, the best option for the organization is to set up a VPN. A Virtual Private Network for employees working remotely is ideal for building a secure place to work. A VPN does not take much effort to set up and is cost-effective. Though VPNs are not cutting edge anymore, they effectively deal with most cyber threats. Ideally, they should be considered the baseline requirement for all organizations having distributed remote teams working for them.
- Employee Training Programs
The pandemic has thrown a challenge to every organization. With teams working remotely worldwide, organizations must be protective of their information assets. Human resource is always the greatest strength of every organization. However, it can also be the weakest. No matter how strong the security policy remains, it comes to nought if not effectively followed or implemented. It is also a failure if employees are not educated about the pitfalls of cyber threats. Hence, the respective organizations’ responsibility is to train their employees on the varied nature of cyber threats in the virtual world.
The threats on which the employees are trained should include the latest ones among malware and ransomware. Also, a thorough workaround of protocols is necessary for everyone in the event of threat detection. Working through unsecured networks needs to be eradicated, and only official networks must be authorized.
- Backing up of Data
This practice is an essential part of any organizational Business Continuity Plan. Backing up data ensures that there is no or minimal loss of data in the event of a network failure or any other catastrophe. Most organizations back data on an hourly basis to prevent a long road to recovery if there is a system malfunction. Reliable data center backups are necessary for the remote workforce. For traditional offices, backups generally conventionally take place, and the response time is standardized. However, in an environment where most work is distributed remotely, the first victim to a network’s failure is the data itself, primarily because there is a lack of communication between teams.
Loss of data may also occur due to the presence of malware or ransomware. These tools are designed to disrupt the normal flow of work. Once malware or ransomware gets downloaded onto the system, the organization may get locked out of its critical data, may even be gone permanently provided there is no backup of the same.
The Security team must also ensure that the backup tools are updated and not antiquated systems that cannot survive the onslaught of modern-day data processing. Enterprises have to invest in these essential mechanisms to provide a stable work environment to their remote employees.
- The Access and Entry Roles
Access control is a fundamental and critical activity undertaken by the Security Centre. In a secure system, most accesses provided are on a ‘need to know’ basis. Access control is essential since organizations work with sensitive data. If data falls into the wrong hands, then all hell may break loose. The management and the IT Security teams’ responsibility is to ensure that only the essential staff are allowed to access critical data. Mere access control may not be the answer to preventing untoward cyber incidents. However, by limiting the number of people getting access to essential functionalities and data, the organization can effectively control the fallout, if any.
Access control also includes the creation of roles, and this is of utmost importance. A particular role decides the limit of the access. For example, an executive can only view data and not edit it, while a super admin or manager can view all data, edit it, and store them in the respective files. Limitation of access prevents costly mistakes that may occur while handling sensitive data. One of the pitfalls of unhindered access is the risk of data deletion. It is a real threat that every data controller fears. The greater the number of people having access to a large amount of data, the greater the possibility of accidental manipulation.
- Two-Step Authentication
It is a must-have security feature that every IT Security team should provide to the employees. A two-step authentication defeats most efforts of malicious actors in trying to break into secured networks. A two-step authentication, which is a subset of multi-factor authentication, is an essential process. Remote access control becomes tricky since the IT Security team’s response time may be delayed compared to the onsite response. To eliminate the chances of unlawful network penetration, organizations must start implementing the two-step authentication process.
- Implementation of Strict Security Guidelines
Enterprise policies keep changing according to the changing scenarios. The pandemic has thrown open a new normal with immense possibilities. However, since various security threats also accompany it, all organizations need to implement appropriate security guidelines. Employees must also follow the guidelines strictly since they are only useful when observed earnestly.
Final Words
As the pandemic continues to compel organizations to transform the work culture to a more remote-based setup, there will be challenges along the way. Data security is of utmost concern, and any failure will have serious consequences. Organizations must have a deep awareness of the scenario and understand the possibilities leading to a data breach. They must also implement necessary cybersecurity policies and procedures to stay secure from any cyberattack that may befall the remote work setup.
References
-
Susan Bradley, Eight key security considerations for protecting remote workers, April 13, 2020, CSO, https://www.csoonline.com/article/3531963/8-key-security-considerations-for-protecting-remote-workers.html
2. Liam McIvor Martin, What Does Fully Remote Work Mean (2021 Guide), Time Doctor, https://biz30.timedoctor.com/what-does-fully-remote-work-mean/
-
Nicky Daly, 7 Tips for Avoiding Remote Work Security Risks, April 6, 2020, Wrike, https://www.wrike.com/blog/tips-avoid-remote-work-security-risks/
-
Lifesize, Distributed Workforce Security Tips, https://www.lifesize.com/en/distributed-work-hub/distributed-workforce-security-tips
-
Kaylie Gyarmathy, 10 Strategies for Securing Your Remote Workforce, October 15, 2020, vXchnge, https://www.vxchnge.com/blog/securing-your-remote-workforce
-
Jeff Petters, Top 5 Remote Work Security Threats, August 12, 2020, Varonis, https://www.varonis.com/blog/top-5-remote-work-security-threats/

