The post-pandemic digital world is facing an exceptional threat from ever-rising cyber crimes such as phishing attacks. Organizations need to learn more about the threat of phishing and take immediate precautions to protect their sensitive and confidential information assets and virtual workforce.
The pandemic has seen organizations worldwide shut down in a way that was never seen before in recent history. On top of the expected slow economic growth problems, there has been an explosive growth of cybercrime during the months following lockdowns worldwide. Consider this – the United Nations reported a 350% rise in the number of phishing websites in the first quarter of 2020 alone; almost no sector remained untargeted.

Some Important Recent Phishing Statistics
Cybercrime is expected to rise in the following months due to the massive rise in reliance on working from home. The worst threat of these emerging risks is phishing. Verizon’s Data Breach Report indicated that 94% of all malware is delivered via emails. Even the healthcare industry is now at the crosshairs of adversaries globally; Netwrix found that phishing has moved up from the sixth most significant cybersecurity concern for healthcare organizations to the single greatest risk. Before we delve deeper into phishing, its types, and safeguards against it, let us have a look at some important phishing statistics.
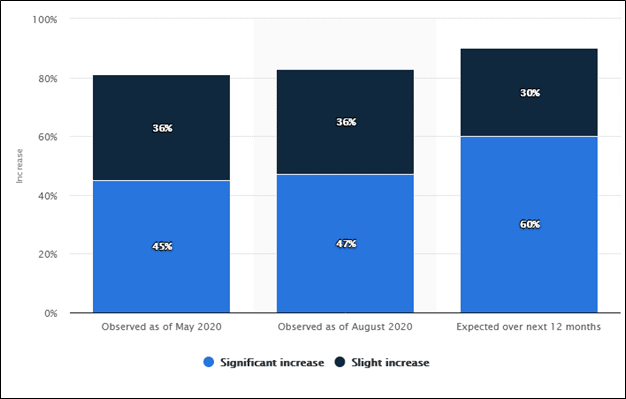
Increase in Cyberfraud after the Coronavirus Outbreak
Some Important phishing statistics from the past few years are given below. They can help organizations understand the need for taking precautions.
- 88% of organizations worldwide experienced a spear-phishing attack in 2019
- 97% of users cannot recognize sophisticated spear-phishing attacks
- Users open 30% of all spear-phishing emails, while 12% of these users click on the links in such emails
- Just one spear-phishing attack can cause losses of up to $1.6 million
Phishing: The Ever-Increasing Threat In Types And Forms
With the improvement of technical defenses, cybercriminals are shifting to social engineering attacks as a preferred means of compromising institutions. Social engineering involves manipulating users using psychological triggers such as fear, curiosity, and greed and lure them into disclosing the PII (Personally Identifiable Information) or financial details such as their bank account details, credit card numbers, and so on.
Phishing is the most well-known example of social engineering. In a phishing attack, adversaries target victims through emails, phone, or text messages to get them to divulge confidential information. They pose as authoritative or trusted entities such as banks, law enforcement, or higher management and demand sensitive information like passwords.
The Most Common Types of Phishing Methods
- Phishing Email: Most phishing attacks are carried out using emails where adversaries try to entice users into clicking a maliciously modifies URL or attachment.
- Vishing: Phishing can also take place using voice messages (Vishing). Twitter was recently a victim of a vishing attack that compromised admin accounts in the tech giant.
- SMS based Phishing: SMSishing uses SMS messages to conduct attacks and works the same way as phishing.
- Spear Phishing: In a spear-phishing attack, adversaries send out an email tailored to appeal to a single individual. Such emails contain personal information and seek to get users to click on a phishing link.
| A Concerning Development
A.I-based deepfake phishing attacks are even more concerning as realistic voice messages can now be sent by adversaries. One example is an attack in the U.K. where cybercriminals impersonated an energy organization’s CEO using A.I. and caused losses worth $243,000. |
How Has Phishing Affected Organizations in the Pandemic
Several organizations have suffered from an increasingly larger number of cyberattacks such as phishing.
One profound change that has occurred due to the pandemic is work from home. With the rise in work from home, the number of attack surfaces for adversaries to exploit has increased tremendously. Zoom phishing scams are a prime example of this. In a Zoom phishing attack, adversaries send seemingly official emails purporting to be from Zoom claiming that a user’s account has been suspended or meetings have been missed. When a link is clicked, malware may enter the system.
Phishing, Spear phishing, and Business email compromise (BEC) is the most common threat vectors for cybercriminals in the healthcare sector. Phishing was part of 59% of all significant security incidents in all organizations and 69% of hospital incidents. Healthcare organizations have suffered the highest cost associated with a data breach among all industries for ten years in a row at $7.1 million in 2020. Healthcare providers also have to
pay $429 per breached record.
Phishing attacks on the healthcare sector have two motives –
- Deliver Ransomware: Ransomware in the healthcare sector is lucrative as healthcare organizations would rather pay up a ransom than risk losing a patient’s life.
- Steal PHI: Cybercriminals seek PHI (Protected Health Information) as it can be used for making false identities, getting free healthcare treatment, and doing insurance fraud.
Federal agencies like the FBI and Cybersecurity and Infrastructure Agency (CISA) have warned healthcare organizations of the threats they face due to adversaries taking advantage of the pandemic.
These agencies issued a joint advisory based on “credible signs of an imminent and increased cybercrime threat to American healthcare providers and hospitals.” The advisory warns organizations that cybercriminals are targeting the sector with malware. It also said that the attacks might lead to data theft, ransomware infections, and disruptions in services.
In the advisory, phishing was named as the most common threat to healthcare organizations. Some COVID related cyberattacks related that led to this advisory include:
- A German patient recently died as they could not be admitted to Duesseldorf University Clinic due to an ongoing cyberattack.
- Post April 2020, Hospitals in Georgia, Missouri, and Michigan have reported phishing attacks that resulted in the exposure of 220,000 confidential medical records.
- Employees at several Boston hospitals received phishing emails that claimed to be from the Department of Health and Health Statistics. The emails requested COVID-19 statistics but were attempts to access systems illegally.
Phishing Threats Faced By Organizations Today
Phishing poses a severe financial risk to organizations in COVID-19 when resources are already scarce. The real impact of a data breach, however, goes beyond just monetary damages. Hidden costs such as brand and reputational damage can take years to manifest.
- Financial Losses: 60% of all organizations shut down within six months of a cyberattack. Nearly 32% of all breaches involve attacks like phishing, contributing significantly to the problem. Ponemon’s cost of a Data Breach report states that a single data breach can cause losses of up to $3.86 million. In the USA alone, a data breach costs approx. $8.64 million.
- Reputational Damages: Aon’s Global Risk Management Survey 2019 finds that reputation or brand damages are the number one cyber risk for organizations. Looking at some significant data breaches that happened over the last few years shows that organizations suffered significant reputational damage that impacted their stock’s value and ability to keep and attract clients.
- Stock Slides: Cyberattacks such as phishing can cause significant stock slides in the short and long term. Capital One is a recent example where after suffering a significant data breach that ultimately cost around $150 million, the share slid by 6%. Aon shows that some organizations have a 25% drop in market value over the year after a cyberattack. Twitter’s spear-phishing attack caused the stock to drop by 1.2%.
- Loss of Clients: Cyberattacks like phishing lead to loss of clients. A recent study by Radware showed that 43% of organizations that suffered from a cyberattack had negative customer experiences and reputational losses. Another study showed how 33% of clients would stop working with organizations that suffered from cyberattacks, and some studies went up to 70%. The best example is how TalkTalk, a U.K.-based firm lost 100,000 clients and a third of its value after a breach.
- Regulatory Risks: Ponemon has pointed out that the damages from a cyberattack are more significant for organizations with regulatory barriers such as finance, healthcare, pharmaceutical, and energy. Legal judgments, fines, settlements, and penalties can add heavily to the overall costs.
- Cyber Espionage: Loss of Intellectual property and cyber espionage can occur due to spear-phishing attacks. Verizon’s Data Breach Investigation Report 2018 showed how 74% of cyber-espionage actions in the public sector had phishing elements. A recent example is how Iranian spies from the Charming Kitten Advanced Persistent Threat group targeted think tanks, universities, and other institutions over Christmas with false text messages. Other governments are also actively targeting pharmaceutical organizations with the intent of stealing information about the vaccine, according to a report by the NSA, CISA & NCSC.
How to Safeguard Against Phishing After the Pandemic
Phishing attacks are projected to keep rising even in the post-pandemic era. The following methods can be used to safeguard against phishing in the pandemic era:
- Identity And Access Management: It is a system of tools and policies security departments to ensure that resources are used appropriately only by authorized users. The Principle of Least Privilege (POLP) is vital to IAM. According to POLP, a user’s account must have only those access rights necessary to execute their roles and responsibilities. POLP prevents the collection of unchecked access rights over a user account’s life cycle, also known as privilege creep. IAM uses the core features of authentication, user management, authorization, and central user repository.
- Use An Email System With Advanced Security Measures: Using a standard world-class email service system that comes with embedded advanced anti-phishing measures can help safeguard against phishing. Such systems provide additional protection for email attachments and link with their “safe links” and “safe attachments” features. The dedicated anti-phishing solutions scan links to determine if they are safe and redirect users to real websites once a link is clicked. If a link is malicious, it is blocked after the user is provided an alert. The safe attachment feature works similarly, and malicious attachments are replaced after the user is notified.
- Employee Security Awareness Programs: Employees are often the weakest links in an organization’s defenses against phishing. However, with proper security awareness training, they can become an organization’s biggest asset against cybercrime. Employees should be trained to recognize and react to phishing emails. The most vulnerable employees should also be identified and provided training according to their level. Simulated attacks, red-teaming, and blue-teaming exercises, and active training are recommended.
- Implement Organizational Policies That Dissuade Phishing: Consider preparing and implementing policies regarding employees’ information that an organization makes public. Lesser data on social media means that there will be fewer spear phishing attacks. For instance, not putting org-charts on corporate websites may prevent adversaries from developing profiles on vulnerable individuals. Employees should also not disclose too much personal information on social media. Data mining sites allow access to information at very cheap costs, and emails can be mined from sites like LinkedIn, requests should be made to take down such information.
- Use SPF, DMARC, and DKIM: Sender Policy Framework helps domain owners protect their domains from being spoofed. Essentially, it verifies a sender’s I.P. address against registered I.P. addresses for that email’s domain and prevents emails that do not match. Thus, adversaries cannot spoof domain names to send phishing emails. Domain Keys Identified Mail (DKIM), on the other hand, works using public keys and private keys to ensure the authenticity of emails. DMARC enables senders to take care of undelivered emails and designates what to do with such emails that were not verified and authenticated by SPF and DKIM.
- Ensure Protection For Devices and Assets: Each organizational device, including laptops, mobiles, and desktops, should be protected from phishing attacks. Multi-factor authentication (MFA), password policies, and other necessary security measures go a long way in preventing phishing attacks. Every device should also have updated software, antivirus, and firewall protection.
- Penetration Testing and Incident Response: Audits and services like Vulnerability scanning, penetration testing, and ethical hacking can help organizations find flaws in their security posture so that they can rectify them. Organizations should also have effective response plans to ensure that they can rapidly respond to attacks in progress and mitigate outcomes. There should be a well-defined process for staff to respond to incidents.
Conclusion
In extraordinary times, we need a renewed focus on ordinary solutions such as awareness training programs, IAM, SPF, firewalls, penetration testing, and more. Organizations must also balance security needs with business objectives. An agile threat management system and an enterprise security infrastructure will be necessary to counter-attack phishing attempts in the post-pandemic world.
References:
-
Ponemon Institute, Cost of Data Breach, 2020,
https://www.ibm.com/security/digital-assets/cost-data-breach-report/
-
Johnson, J., Global increase in cyber fraud risk since the coronavirus outbreak as of August 2020,
https://www.statista.com/statistics/1175574/increase-cyber-fraud-coronavirus-outbreak/
-
National Cyber Security Centre, K. and allies expose Russian attacks on coronavirus vaccine development
https://www.ncsc.gov.uk/news/uk-and-allies-expose-russian-attacks-on-coronavirus-vaccine-development/
-
GreatHorn, 2020 phishing attack landscape report, Cybersecurity Insiders,
https://info.greathorn.com/report-2020-phishing-attack-landscape
-
Business Standard, N. reports a sharp increase in cybercrime during coronavirus pandemic, United Nations,
https://www.business-standard.com/article/technology/un-reports-sharp-increase-in-cybercrime-during-coronavirus-pandemic-120080700289_1.html
-
Dhwani Meharchandani, Staggering Phishing Statistics in 2020,
https://securityboulevard.com/2020/12/staggering-phishing-statistics-in-2020/#:~:text=More%20than%2060%2C000%20phishing%20websites,are%20intended%20for%20intelligence%2Dgathering.&text=1%20in%20every%202%20organizations,in%2073%25%20of%20these%20attacks.
-
CISA, Alert (AA20-302A) Ransomware Activity Targeting the Healthcare and Public Health Sector,
https://us-cert.cisa.gov/ncas/alerts/aa20-302a
-
Verizon, 2020 Verizon Data Breach Investigation Report,
https://enterprise.verizon.com/en-nl/resources/reports/dbir/
-
Fast Company, Never click on such Zoom invites. You’ll thank us forever,
https://www.fastcompany.com/90582864/never-click-on-this-kind-of-zoom-invite-youll-thank-us-forever#:~:text=and%20ruin%20you.-,Zoom%20phishing%20scams%20are%20the%20latest%20conduit%20for%20planting%20malware,passwords%2C%20and%20empty%20bank%20accounts.
-
Chris Brook, How much Do Data Breaches Cost Organizations in 2020?
https://digitalguardian.com/blog/what-does-data-breach-cost-2020
-
Scott Steinberg, Cyberattacks now cost companies $200,000 on average, putting many out of business,
https://www.cnbc.com/2019/10/13/cyberattacks-cost-small-companies-200k-putting-many-out-of-business.html
-
James Trainor, Reputational risk and cyber attacks go hand in hand,
https://www.aon.com/unitedkingdom/insights/reputational-damage-and-cyber-risk.jsp
-
Spamtitan, New Research Reveals Extent of Reputation Loss After a Cyberattack,
https://www.spamtitan.com/web-filtering/new-research-reveals-extent-of-reputation-loss-after-a-cyberattack/
-
Joe Warminsky, Iran-linked spies used Christmas as cover for spear-phishing, researchers say,
https://www.cyberscoop.com/iran-espionage-charming-kitten-certfa/
-
Himss, 2019 Himss Cybersecurity Survey,

