Organizations are increasingly focussing on adopting healthy practices and maintain a secure ecosystem to shield themselves from anticipated cyber-attacks. Cybersecurity tools are an integral and indispensable part of a robust cybersecurity strategy. An organization has a choice of a variety of cybersecurity tools.
 Protecting the critical information infrastructure and valuable information assets are essential for every organization, big or small. Malicious actors inside or outside of the organizational periphery, phishing and other cyberattacks, malware, and viruses can be colossal security threats to the computing environment. Authorities must protect every system in the organizational infrastructure lest malicious actors should make their mark and breach the network, compromising the confidentiality, integrity, and availability of critical or sensitive data. According to an organization’s varying needs, there are various types of cybersecurity tools available, from the plug-and-play security resources to solutions that need to be installed on the system.
Protecting the critical information infrastructure and valuable information assets are essential for every organization, big or small. Malicious actors inside or outside of the organizational periphery, phishing and other cyberattacks, malware, and viruses can be colossal security threats to the computing environment. Authorities must protect every system in the organizational infrastructure lest malicious actors should make their mark and breach the network, compromising the confidentiality, integrity, and availability of critical or sensitive data. According to an organization’s varying needs, there are various types of cybersecurity tools available, from the plug-and-play security resources to solutions that need to be installed on the system.
Today, having a single line of defense is not sufficient for an organization. Enterprises need multiple weapons in their arsenal to be safe and not sorry! Advanced cybersecurity framework and strategies leverage a layered security approach (defense in depth), which means having multiple lines of defense. Enterprises must also possess end-to-end security at various IT ecosystem levels such as Data, Network, Host, Perimeter, and Application.
Unearthing Vulnerabilities: How Do Cybersecurity Tools Help Organizations?
Most individuals and organizations are concerned about being potential victims of a cyberthreat or online fraud in one way or another. The following graph portrays the scenario well. Over 80% of respondents fear that they do not have any control over the data collected by them through online means.
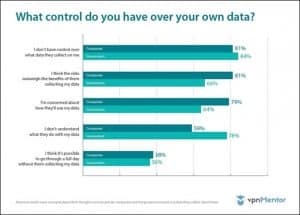
Such statistics emphasize the necessity of deploying a robust cybersecurity policy for any organization. Security tools in modern architecture revolve around multiple defense layers. They deploy numerous obstacles in the malicious actor’s path to make them give up trying to infiltrate the system. These cybersecurity tools help enterprises in:
- Security Management
They perform several tasks like overseeing security functions, performing risk assessment, ensuring operational compliance, sensitizing end-users, and changing management processes and procedures.
- Identity and Access Management
The cybersecurity tools implement robust IAM, including procedures, systems, and processes to manage authentication, access controls, and assign identities. The identification system includes setting up the respective user with unique names. Authentication involves defining a method for these users to prove their identity.
- Security Engineering
Security Engineering is divided into network security and operations security. The cybersecurity tools fulfill responsibilities around email filtering, endpoint data loss protection, intrusion detection, router security, firewall, DLP, and antivirus.
- Business Continuity
These tools help organizations be resilient and act to recover for the business operations if they undergo an attack or a natural disaster. They curate procedures to restore all the critical functions with the least data and time loss.
- Information Security Regulatory Compliance
Some cybersecurity tools help oversee security controls to ensure that they comply with industry standards and regulations. They include understanding the nuances of changing statutes to implement appropriate security controls.
- Software Development Security
It is an aspect of cybersecurity tools that address the inherent issues of an application or system. It includes imparting security training to software developers, overseeing the development process, performing code analysis, and analyzing future threats it may face.
The 7 Best Cybersecurity Tools Available Today
The advantages of deploying a robust cybersecurity policy are undebated, and cybersecurity tools form a crucial part. Given below are the top cybersecurity tools that organizations have access today:
- Firewalls
Firewalls form the core of cybersecurity tools, and they act as the first line of defense against numerous incoming threats, such as malicious data packets. Their main aim is to prevent unauthorized access to a private network. They can be deployed as software, hardware, or both to prevent malicious actors from getting unauthorized access into such a network. All messages pass through the firewall, which examines each of them and subsequently allows or blocks them. Messages not meeting specified security criteria are the ones that will be restricted.
Although firewalls are advantageous, they have limitations too. Malicious actors are becoming smart and develop sophisticated programs that may pass through firewalls. However, firewalls act as a robust first line of defense against less sophisticated attacks. An example is:
It is a powerful internet security suite that offers a variety of featured security protections. It includes a robust firewall and antivirus protection that also prevents ransomware attacks.
Some other features of Bitdefender are anti-theft, anti-fraud, and anti-phishing options. It also offers a performance optimizer and privacy protection options like file encryption, parental controls, anti-tracking, and microphone protection to prevent misuse by a third party. The internet security suite protects Windows users and prevents attacks on macOS, iOS, and Android devices. Additionally, users don’t need a separate license for each of their devices, and a single product license gives protection on five devices!
- Antivirus Software
Antivirus software refers to programs designed to primarily detect, prevent, and remove viruses on organizational information resources, IT systems, and networks. It also offers protection to systems and networks against threats like spyware, botnets, ransomware, adware, trojan horses, browser hijackers, worms, keyloggers, and rootkits. Most antivirus software check for automatic updates regularly and have an auto-update option. Thus, they keep recognizing new threat patterns and offer updated protection. Additionally, they also provide services like email scanning to check for malicious web-links and attachments. An example is:
It is an award-winning service that offers unmatched protection against critical threats like viruses, malware, and malicious intrusions. It incorporates privacy and protection tools that guide an organization to protect their devices from every angle. While some devices will not support all the features, every protected device gets the best security within the technological constraints and device-specific limitations. Some features of Kaspersky Complete Security are:
- Protective detection to identify device vulnerabilities and threats.
- Real-time protection to block threats before they attack a device.
- Instant neutralization to quarantine and remove malicious threats.
- PKI Services
PKI or Public Key Infrastructure is a cybersecurity tool that supports the identification and distribution of the public encryption keys. It allows enterprises and systems to verify vendors, customers, and clients’ identities and exchange data securely over the internet. Although they can by-pass PKI to exchange sensitive information, authentication from the other party is not guaranteed in such cases.
Some organizations associate PKI with TLS or SSL, which are technologies responsible for encrypting server communication. If a website’s security certificate is verified, they display a padlock in the browser’s address bar. Thus, PKI acts as the solution to many problems and form a part of an enterprise’s overall cybersecurity strategy. A summary of the uses of PKI is listed below:
- It is used to enable access control and Multi-Factor Authentication.
- It helps create trusted and compliant digital signatures.
- It helps enterprises authenticate sender identity and encrypt email
- It is used to protect and digitally sign the code.
- It helps build trust and identity in IoT ecosystems. An example of a PKI service provider is:
The inherent ability to develop and manage a PKI depends upon the skills and knowledge of the people handling it. PKI Solutions Inc. offers training that focuses on building skills and knowledge of Microsoft Active Directory Certificate Services (ADCS). They put a strong emphasis on best practices and hands-on skills for security. They offer up to date PKI training for Windows Server 2019, 2016, and 2012 R2 versions.
- Managed Detection And Response Service (MDR)
Malicious actors are getting advanced, and they use the latest software and techniques to breach an organization’s network. Thus, every enterprise needs to use robust cybersecurity defenses. Managed Detection and Response, or MDR, refers to an advanced security service that offers threat intelligence, incident analysis, security monitoring, threat hunting, and incident response. It is most suitable for organizations that lack adequate resources, like SMEs but want to be aware of the risks and improve their threat detection and response capabilities. The managed detection and response uses AI and ML to auto-detect, investigate, and orchestrate a quick response to threats.
MDR possesses the following characteristics:
- Puts focus on threat detection.
- Relies heavily on advanced analytics and security event management.
- While most processes are fully automated, it also incorporates humans for monitoring activities.
- Service providers perform remote response and incident validation. An example is:
A combination of MDR services, XDR, and response automation, Cynet 360 can be termed the perfect Autonomous Breach Protection solution. The Cynet platform comes with CyOps, a 24/7 MDR team comprising best threat analysts and security researchers. The following are the features of Cynet 360:
- Cynet MDR offers 24/7 alerts, monitoring, proactive threat hunting, investigations, detailed threat reports, and robust incident response.
- It natively integrates UBA, NDR, EDR, NGAV, and other deception technologies to offer complete detection, response, and prevention.
- It investigates the threats to the root cause and removes them from all infected hosts.
- Network Security & Monitoring Tools
These tools help IT security teams perform regular scans and detect unexpected changes and flaws in the information systems. They simplify network monitoring and administration and also help maintain security compliance through routine audits. Firewalls, antivirus programs, and intrusion detection systems are the peripheral network security solutions that keep networks safer. Port scanners, packet analyzers, and network mappers are the network security utilities used in penetration testing. Thus, administrators can identify the inherent vulnerabilities in their network, which malicious actors could exploit to carry out DNS spoofing and DDoS attacks. An example is:
It monitors the systems, networks, and hosts to deliver real-time alerts to the administrators. Users can select the notifications they want to receive. Nagios monitor network services like HTTP, SMTP, POP3, NNTP, ICMP, etc. It is a powerful and free network monitoring tool that all kinds of organizations can deploy.
- Vulnerability Scanning And Penetration Testing (VAPT) Tools
A Pen-test or Penetration test is a crucial way to evaluate an organization’s security systems and IT infrastructure. During a Pen-test, IT security teams try to mock-exploit the inherent vulnerabilities safely. Such vulnerabilities reside in services, applications, operating systems, risky employee behavior, and improper configurations. Cybersecurity professionals use techniques and processes that are similar to the ones deployed by malicious actors to detect areas of weakness and potential threats.
Pen-tests attempt the type of attacks an enterprise might face from malicious actors, such as phishing, code injection, and password cracking. The tests can be carried out using either automated or manual technologies to evaluate web applications, wireless networks, network devices, servers, mobile devices, endpoints, and other potential vulnerability points. After performing the penetration test successfully, the testers present the administrators with detailed reports and findings, including recommendations for the system’s possible changes. An example is:
It is a lightweight network scanner that can carry out Penetration tests on organizational systems. It can scan both small networks and the internet.
- It is a free tool that can be used for gathering baseline details of the network.
- Best use cases are the initial triage of an attack and information gathering. Only Linux platforms and macOS supports Zmap.
- Employee Training As A Tool
While one cannot define staff training as a cybersecurity tool, knowledgeable employees who understand cybersecurity act as a robust primary defense line against potential threat vectors. Enterprises can use many training tools to educate their staff about cyber hygiene and cybersecurity best practices.
Since malicious actors are rapidly modifying and improving their techniques and carrying out sophisticated attacks, enterprises need to invest in staff training services and tools. Failing to do so can leave them in a critically vulnerable position open to attacks by malicious actors. A little added expense will offer more significant dividends in security and protection in the long run.
- After attending these training sessions, employees will be better positioned to understand their crucial role in maintaining a secure environment.
- It will help management send a message to the employees that they are serious about cybersecurity, and help build a cyber aware culture.
Final Words
It is clear that the greater the number of cybersecurity tools IT professionals use in their work, the higher the chances of addressing security risks. Knowledge of the various cybersecurity tools is just the start, and security teams must know how to implement them efficiently in their organizational ecosystem. Since new security threats keep emerging regularly, enterprises need to deploy dynamic security solutions. It helps IT security teams identify vulnerabilities and ensure data security efficiently.
BACK TO MAIN PAGE
