Cybersecurity issues are becoming a regular menace for most businesses. With the Covid-19 pandemic, the ever-evolving cyberattacks have brought cybersecurity policy-making center-stage for organizations once again. A healthy business is only a dream without an appropriately optimized cybersecurity policy.
Inadequate and weak cybersecurity policies impact the organization and are also problematic for its customers, clients, and the broader market. The consequences can be exceptionally severe if the shortcomings subject an organization to a severe breach that exposes confidential customer data besides compromising the business’s critical data. Therefore, enterprises need to formulate a robust cybersecurity strategy that pans across the spectrum of deployed valuable information assets. Enterprises need to prepare themselves better by implementing robust cybersecurity measures to avoid such instances, and the first one must be to optimize ‘Enterprise Cybersecurity Policy.’
Some Key Statistics On Inadequate Poor Cybersecurity Policies Adopted By Enterprises
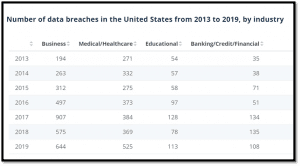
Recent cybersecurity statistics show a tremendous increase in breached data from sources becoming increasingly common in workplaces, like IoT and mobile devices. The below graph shows the increasing number of data breaches in the USA over the past few years.
Following are the key statistics underlining the results of inefficient cybersecurity policies adopted by enterprises.
- According to Cybint Solutions, over 62% of enterprises experienced social engineering and phishing attacks in 2018.
- Another study by Accenture showed that there was an 11% increase in security breaches since 2018 and 67% since 2014.
- Varonis presented a grim scenario saying that over 1000 sensitive files were open to every employee in 53% of organizations.
- Symantec said that there was a 12% rise in enterprise infections in 2018. It further classified the leading email attachments in .doc and .dot format as the primary attack vector leading to 37% of breaches.
- A unique finding put forth by the University of Maryland was that malicious actors attacked 2,244 times a day on average, which is an attack every 39 seconds.
- A combined study by Thycotic and Cybersecurity Ventures suggested an estimate of the number of passwords used by machines and humans at risk in the future. It said that it would cross 300 billion by 2020, which will expose more businesses to risk.
- Research by IBM showed that a breach was identified in 280 days, on average.
What Happens In The Absence Of A Robust Cybersecurity Policy?
An inefficient or inadequate cybersecurity policy of a business organization increases the risk of exposure to cyber threats, which may further have the following consequences:
- Losing Customers: Compromising customer data in an organization’s database can affect the customers’ trust in the business. Gradually, it will see a decline in the number of existing customers as well as potential ones.
- Compromised Inventory Management: The importance of inventory management can be gauged by counting the number of computer systems and applications a business uses to track its inventory. Compromised inventory management can hamper the organization’s ability to perform myriad tasks, like reordering products from the supplier or keeping track of customers’ choices.
- Reduced Resources For Growth: A cybersecurity incident can cost a business dearly and impact its growth. For example, if a business undergoes a ransomware attack, the malicious actors will lock access to its systems until the executives’ pay the ransom. The amount paid as ransom will have its impact as a reduced budget for further development plans.
- Loss Of Business: A cybersecurity incident will hamper crucial aspects of operations, and the organization will be unable to serve its customers. For example, if a hospital’s systems get compromised, they may have to send the patients elsewhere.
- Regulatory Penalties: If an enterprise operates in a jurisdiction covered by GDPR, interacts with customers, and doesn’t have an adequate cybersecurity policy in place, it can be fined by the privacy regulator when it faces a data breach. Other privacy regulations are the California Consumer Privacy Act (CCPA), the National Institute of Standards and Technology (NIST), etc.
10 Security Tips To Optimize Your Cybersecurity Policy
Crashed websites, intercepted emails, breached networks, compromised devices, stolen credit card data, denial of services and other cyber threats are the direct consequences of a weak cybersecurity policy. An effective cybersecurity policy must help the enterprise become:
- Secure: A secure enterprise will prioritize the digital asset value, focussing on aspects that matter the most. Since it is nearly impossible to design a completely secure network, such enterprises allocate the organizational resources according to the asset value. They obtain a security level corresponding to that value.
- Vigilant: It includes making employees aware of how they may inadvertently expose the organizational data to threats through online conduct, mobile devices, and social media. A vigilant cybersecurity approach includes gathering threat-intelligence and evaluating the type of hazards that can damage the enterprise. The information also helps in cyber threat monitoring. Other critical factors for maintaining vigilance are training, policy development, and fixing accountability.
- Resilient: A resilient enterprise will reduce any impact on its stakeholders and restore operations quickly following an incident while maintaining credibility and security. Rapid detection and well-structured response plans help organizations maintain resilience. The recovery plans must define clear roles, actions, and responsibilities to limit the damage and mitigate future risk.
A robust cybersecurity policy is one that possesses the above qualities and more. Here are ten essential tips that help an organization optimize its cybersecurity strategies to achieve it.
- Knowing Which Assets Need Protection
Knowing what you need to protect is the first step to draft a robust IT security strategy. Answering the following questions can help business executives understand the critical assets in their infrastructure that need attention.
-
- Which are the most valuable information assets?
- Where are they located?
- Who can access them and why?
- How often are they being accessed?
Thus, IT security teams can get insights into the enterprise’s standard system operations, which will help them detect abnormal patterns. Knowledge of assets also includes evaluating business partnerships and relationships to identify vendors and third parties that may provide malicious actors with accidental access to the organizational data. Thus, it requires close collaboration among security, IT, and business executives.
- Evaluating The Security Posture
Malicious actors will never stop looking for and exploiting vulnerabilities. As long as there are exploits, enterprises need to implement processes for finding and remediating the vulnerabilities. Thus, continuous vulnerability assessment must form an integral part of the cybersecurity strategy.
However, a vulnerability assessment is valuable only if the CISOs and IT security executives weigh it in the context of the existing security infrastructure. Only then can they analyze the assessment output and apply the knowledge to develop a robust cybersecurity policy. Such an approach will justify the security budget and strengthen the enterprise’s overall compliance and security posture.
- Taking A Data-centric Approach
To protect themselves from the evolving cyber-attacks, enterprises need to shift their focus from preserving everything to securing the most crucial aspect – sensitive data, irrespective of where it is used, transmitted or stored. Following the basics can help streamline the data protection process.
Organizations must identify sensitive data, locate where it resides, draft policies to handle it, educate employees about the potential threats, and implement adequate technical controls. Thus, they can maintain greater control over critical data by classifying them effectively, determining what’s valuable, and preventing common pitfalls.
- Developing A Clear Understanding Of The Security Issues In Cloud Service Models
Cloud service models offer a range of benefits like scalability, increased flexibility, and productivity to businesses. However, some deployments suffer from associated security complications. Although cloud models are not fundamentally insecure, organizations need to manage them securely. They must develop a clear understanding of cloud computing and associated models as security issues vary according to different models.
- Addressing Insider Threats
Most people label malicious actors, terrorists, organized crime groups, and rival nation-states as the perpetrators, but they don’t realize that insider threats can prove more damaging and costly. It is so because the insiders have the means to gain access to the most critical data. Hence, it is not sufficient to merely look outwards or focus on outsider threats; IT security teams must monitor what is happening inside the enterprise with equal seriousness. In today’s world of stiff competition, the rivals can be lurking at any corner.
Another strategy to prevent insider threats is educating the workforce about various cyber threats and ways to protect organizational data. While social media can help gain leads and customers, employees must know how to generate insights without falling prey to malicious interventions. They must be informed about communicating online successfully without disclosing confidential information to the competing business or public.
- Leveraging Threat Intelligence
Knowing the malicious actors before they strike can act as the best line of defense against cyber-attacks. While the collaborative defense method has been a talking point for national security, it is also gaining importance in IT security. But sometimes, it becomes difficult for businesses to gather quality intelligence. Hence, they can approach commercial vendors who can arm them with tactical, strategic, and operational insights. These perspectives will help them identify and respond to threats and secure their networks.
For instance, sometimes work doesn’t seem productive, and John decides to visit a coffee shop nearby to unwind. The shop offers free Wi-fi, and he immediately connects to it. Although it may seem tempting, John’s connecting to the unsecured network opens the doors for malicious actors to breach the enterprise network. The threat intelligence will gather insights about the potential for employees like John to leak critical information and suggest encrypting data or implementing a firewall to secure the business network.
- Improving Password Protection
It is a no-brainer that enterprises need to use a password to protect their networks. A robust cybersecurity policy takes password protection a step further and suggests regularly changing critical passwords. IT teams must go beyond letter and number sequences and implement multi-factor authentication as an added security measure. It requires more doors to be unlocked other than a single password to allow entry.
- Monitoring Personal Devices Used By Employees
All organizations do not have sufficient resources to provide their employees with smartphones, laptops, and tablets. Hence, many of them choose the economical way and ask their staff to use their devices to collaborate and access the organizational systems and data. If so, the businesses must implement a policy that gives the network administrator system access to monitor software, install security updates, and make routine password changes on their devices.
It is not a question of invading employees’ privacy but of protecting a business. Additionally, enterprises can establish guidelines that educate employees on safeguarding sensitive data and other identifiable information. It can include adding multi-factor authentication, limiting access, security questions, encryption, etc. Employees must understand the consequences if they do not follow the organization’s cybersecurity policies.
- Filling Skill Gaps Through Managed Service Partners
Managed security services help augment the organization’s IT security teams. They also reduce the capital required to hire, train, and retain the security personnel for maintaining a robust security posture.
These providers offer enterprises the options and flexibility required to bring their cybersecurity posture in line with the ever-evolving regulatory requirements. They monitor the devices and IT infrastructure at the service level and support vital security programs without interfering with their policies and incident management.
- Devising Comprehensive Incident Response Plans And Preparing For The Inevitable
Enterprises keep focussing their IT security spending and efforts on cyber-attack prevention, but they often forget to prepare for the inevitable. They can define a comprehensive incident response plan to aggressively respond to an attack, align their defenses, minimize damage, and mitigate future intrusions.
Final Words
Malicious actors of today are becoming skilled at orchestrating large-scale attacks on their victims. Enterprises with numerous vulnerabilities and inefficient cybersecurity policies are their favorite targets. Hence, future-oriented enterprises geared up for growth and success cannot afford to ignore the importance of deploying a robust cybersecurity plan.
As per research by Gartner, the global information security market will touch $170 billion by 2022. It indicates that more and more organizations are becoming cyber security-conscious today. However, there is still a long way to go, considering the vastness of the current cybersecurity landscape’s insecurities.
BACK TO MAIN PAGE
